Free Online Tools for Examining Suspicious PDFs
Free online tools automate suspicious PDF analysis without local installation: QuickSand for manual structure exploration, Jsunpack and Wepawet for JavaScript deobfuscation, and Gallus for exploit identification. Multi-engine scanners like VirusTotal check if antivirus products flag the file as malicious.
In an earlier post I outlined 6 free local tools for examining PDF files. There are also several handy web-based tools you can use for analyzing suspicious PDFs without having to install any tools. These online tools automate the scanning of PDF files to identify malicious components. The list includes QuickSand, Jsunpack, Wepawet and Gallus.
QuickSand
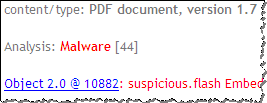
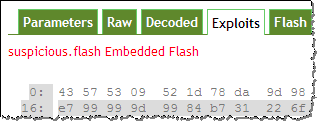
QuickSand by Tylabs is able to scan the uploaded PDF for several known exploits, allows the user to explore the structure of the file, as well as examine, decode and dump PDF object contents. This tools lends itself well to manual PDF analysis tasks. In this way, it differs from Jsunpack and Wepawet, which focus on automating the analysis as much as possible.
Jsunpack
Note: This site is no longer available. The entry below is kept for archival purposes.
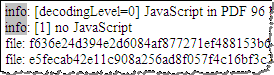
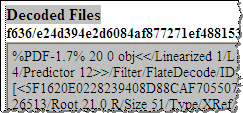
Jsunpack by Blake Hartstein is designed for automatically examining and deobfuscating JavaScript. Its features also include carving contents of network packet capture (PCAP) files and identifying common client-side exploits. It can also examine PDF files for malicious JavaScript artifacts. (The example I uploaded used Flash, rather than PDF, so Jsunpack didn’t locate malicious artifacts in this case.)
Wepawet
Note: This site is no longer available. The entry below is kept for archival purposes.
Wepawet by UCSB Computer Security Lab is an automated tool for identifying malicious client-side components in the form of PDF, Flash and JavaScript elements. (However, it did not flag the PDF file I uploaded as malicious.) Like Jsunpack, its strength is in examining JavaScript for shellcode and suspicious actions.
Gallus
Note: This site is no longer available. The entry below is kept for archival purposes.
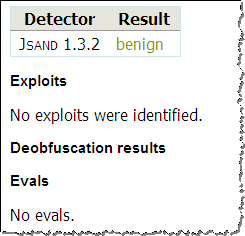
Gallus by MyCERT is an on-line scanner for PDF files, which is able to identify common exploits. Its present implementation seems to focus on JavaScript, and it was unable to identify the PDF sample that included a Flash-based exploit as malicious.
Multi-Engine Antivirus Scanners
If you merely need to know whether antivirus products identify a particular PDF file as malicious, without gaining much insight into the file’s inner-workings, you can upload the PDF to free online services that scan files using multiple antivirus engines. The options include: VirusTotal, Jotti’s Malware Scan and VirSCAN.
Flash and Online PDF Analysis Tools
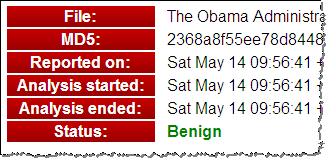
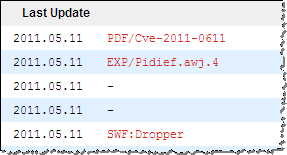
To capture the screen shots above, I used the same “The Obama Administration and the Middle East.pdf” file I mentioned in my posting How to Extract Flash Objects from Malicious PDF Files. While attackers have historically used JavaScript, that file demonstrated a relatively recent technique of launching exploits with the help of Flash object instead.
The automated online analysis tools Jsunpack, Wepawet and Gallus weren’t able to handle Flash-based PDF malware, even though they do really well with JavaScript embedded in PDF files. (This is why using Flash in PDFs is more attractive to some attackers at the moment than utilizing JavaScript.)
Despite this present limitation, there awe excellent tools that can save you a lot of time. I have no doubts that the developers of these tools will adjust them to handle Flash objects more effectively.