Analyzing Suspicious PDF Files With PDF Stream Dumper
PDF Stream Dumper is a free Windows tool with GUI for analyzing suspicious PDFs. It scans for known exploits, navigates object structures, decodes streams, and includes a JavaScript interpreter for deobfuscation. Its shellcode analysis features use LibEmu to emulate execution and identify API call signatures.
Targeting a vulnerability in Acrobat Reader is one of the more popular ways of compromising systems nowadays. PDF Stream Dumper is a free tool for analyzing suspicious PDF files, and is an excellent complement to the tools and approaches I outlined in the Analyzing Malicious Documents cheat sheet.
For this introductory walk-through, I will use a malicious PDF file that I obtained from Contagio Malware Dump. If you’d like to experiment with this file in an isolated laboratory environment, you’re welcome to download the malicious PDF from my server; the password to the zip file is the word “infected”.
PDF Stream Dumper is a self-contained program that runs on Microsoft Windows and contains a convenient graphical user interface. The tool contains numerous features. I will only touch upon some of them here.
Examining a PDF File for Suspicious Characteristics
After installing PDF Stream Dumper, load the suspicious PDF file into it and start looking around. The tool includes a number of signatures of known PDF exploits. To scan the file, select “Exploits_Scan” from the menu:
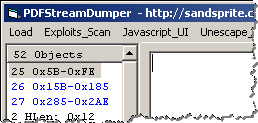
In this case, PDFStreamDumper identifies the exploit and specifies where it’s present in the PDF file:
Exploit CVE-2007-5659 - collectEmailInfo - found in stream: 31
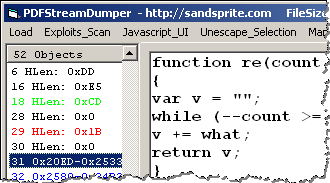
You can use the left pane of the tool to navigate through the file’s objects to examine their contents. The tool will decode steams where necessary. For instance, viewing the steam in object 31 shows us embedded JavaScript:
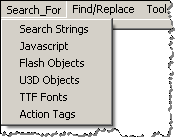
Another way to locate suspicious objects within the PDF file is to use the tool’s “Search For” feature, which can automatically locate JavaScript, Flash objects among other entities:
Examining Malicious JavaScript in the PDF File
When looking at JavaScript embedded in a PDF object, we can click the “JavaScript_UI” button to bring up the interactive JavaScript viewer and interpreter, which is built into PDF Stream Dumper:

Sometimes, the scripts embedded into PDF files are obfuscated. PDF Stream Dumper allows you to run these scripts using the built-in interpreter, which can help you deobfuscate them.
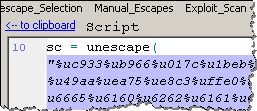
In the example we’re examining now, the script isn’t obfuscated. It seems to contain Unicode-encoded text, which is probably shellcode:
Examining Shellcode Embedded in the PDF File
Shellcode is typically used to store the payload of the exploit—the malicious code that will be executed on the victim’s system. PDF Steam Dumper provides several tools for understanding the capabilities of the shellcode embedded into the file though its “Shellcode_Analysis” menu.
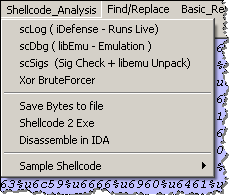
For example, we can select “scSigs” to emulate the execution of the script using the built-in LibEmu engine and look for signatures of the API calls often present in shellcode:
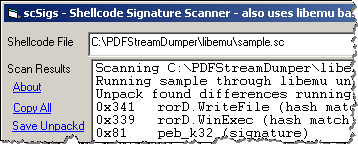
The tool recognizes the signatures of WriteFile and WinExec. This shellcode probably uses these calls to save and execute a malicious windows executable, which it might download from the Internet or which might be embedded into the PDF file itself.
We can get another perspective on the shellcode by running it using the built-in iDefense shellcode logger module “sclog”:
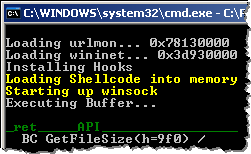
The tool shows us that the shellcode executes the GetFileSize API call. This is often used as part of malicious document files to locate code embedded into the file. Most likely, this shellcode uses GetFileSize to locate the malicious executable embedded into the PDF.
We now are reasonably certain that we’re dealing with a malicious PDF file that exploits the CVE-2007-5659 vulnerability in Acrobat Reader to extract and run a malicious executable embedded in the PDF. We’d need to perform additional steps to extract and examine that executable, but that is outside the scope of this brief note.
If you like analyzing malicious programs, take a look at the Reverse-Engineering Malware course
I teach at SANS. If you’re just getting to know malware, you might also like my Combating Malware course.