A Close Look at PayPal Overpayment Scams That Target Craigslist Sellers
PayPal overpayment scams target Craigslist sellers using fake payment notifications that ask victims to wire funds to a third-party "pickup agent." Scammers craft stories about working in rural areas to explain why they can't make phone calls, and use SMS and email from VoIP numbers and Gmail accounts to avoid revealing their identity.
My hope is that when people become familiar with the tactics employed by scammers, they will be less likely to get ripped off. With this in mind, I’d like to describe my recent interactions with miscreants who target sellers on Craigslist. Perhaps the details I’ve gathered about the scammer’s operation will help curtail such activities. This encounter, which involved SMS messages, emails and a click, is a variation of a PayPal-themed overpayment scam that has been quite prolific in the recent years.
”Working in a very rural area”
The text message from 731-907-0226 arrived in response to my Craigslist post that advertised a furniture item for sale. “Text me back at (7312777303 if you still have it, am interested. Text only”. My ad included a temporary phone number I had set up just for cases like this. Responding to the sender of this message produced no reply; however, when I texted 731-277-7303, I received a quick answer:
“My name is Rick Smith. I am buying this as a surprise,I work with Turner Construction,we are currently working at a very rural area which makes it very hard for me to make phone calls. I have a Mover who will come for the pickup, I will be making the payment via PayPal that is the only payment option.”
This message achieved two critical objectives for the scammer. First, the person began crafting a story that will provide an excuse for asking the victim to wire funds to a third party. In addition, the scammer was establishing a reason why he could not interact with me using voice calls. The supposed buyer was claiming to be in an area where voice calls didn’t work. In another variation of a Craigslist-originating scheme, scammers used the excuse of being on active duty in the military, which precluded non-text communications. Scammers might shy away from phone calls, in part because interacting with multiple targets this way is time-consuming; also, calls might reveal too many details about the miscreant. The scammer also requested my email address, so he could send me payment. He insisted that PayPal was the only payment method he could accommodate. As is common in ploys that target Craigslist users, the scammer didn’t want to contact the victim using the Craigslist email relay, probably to avoid getting blocked by that system. The scammer’s phone numbers above were associated with the VoIP company Bandwidth.com, which makes its virtual numbers available to other providers, such as Google Voice according to Phone Validator.
”You are required to send the $680.00”
After I supplied my email address, which I set up for interactions like this, I received a reply:
“Please check your email for the notification and instructions,but if you don’t get the notification in your inbox please check the spam. PayPal must have sent you some emails by now, I think you need to follow some steps. please check both spam/junk and inbox and get back to me ASAP.”
Indeed, my Hotmail inbox included a message with the subject “Notification Of An Instant Payment From Rick Smith([email protected])”. Although it was designed to look like it came from PayPal, its headers told a different story:
Authentication-Results: hotmail.com; spf=pass (sender IP is 209.85.223.194) [email protected]; dkim=none header.d=consultant.com; x-hmca=none [email protected]
X-SID-PRA: [email protected]
Sender: [email protected]
From: "[email protected]" <[email protected]>
Date: Sun, 30 Aug 2015 19:20:59 +0100
Subject: Notification Of An Instant Payment From Rick Smith([email protected])
Return-Path: [email protected]The headers confirmed that the message was sent using Gmail (209.85.223.194 belongs to Google). The actual sender was [email protected]. All emails I received from the scammer had the Date: header that included the UTC+0100 time zone designation. This is the Central European Time (CET) time zone, which matches several countries in Europe and Africa.
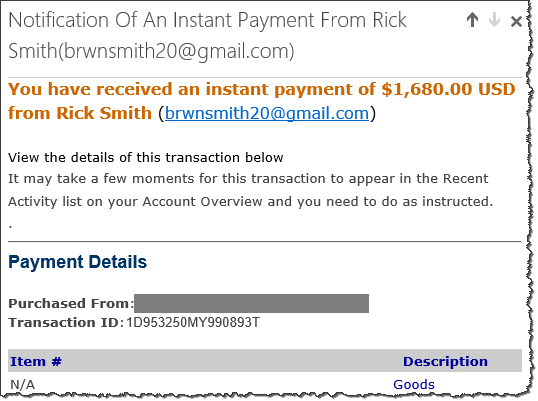
The notice listed the buyer’s address as [email protected], which might be an artifact carelessly left from an earlier version of the scam. The email indicated that the supposed payment was significantly larger than what I had requested on Craigslist. It included an explanation for this overpayment:
“Rick Smith has made his intentions known to PayPal® that he will like $680.00 USD to be sent to the recipient’s address below.You are required to send the $680.00 USD via Money Gram Money Transfer.”
This was a setup for the overpayment scam, in which victims are persuaded to pay a third-party on behalf of the miscreant.
”We are working with Money Gram on this transaction.”
Despite the (fake) email confirmation of payment, no funds were actually deposited into the PayPal account had I set up for such interactions. When I asked the “buyer” about this discrepancy, he explained:
“As per the e-mail PayPal sent to me which is also similar to yours which i hope you receive, you will have to pay an upfront payment out of your pocket via Money Gram to the address given to you, and you will be given the information which is the Reference Number you will email to PayPal by replying to the confirmation mail from them regarding the details you have from Money Gram, you will receive the whole money in your account without any delay.”
The fake PayPal message in my inbox clarified that I might not see the funds in my PayPal account until I sent money to the buyer’s pickup agent using MoneyGram. The email provided further assurances:
“The money has now been deducted from the buyer’s account and is ready to be deposited into your PayPal® account. Please reply this email directly with the Information needed from you. While funds are pending, the money belongs to you but is not available to spend or withdraw.”
Soon, I received two more messages claiming to be from PayPal and impressing upon me of the safety of the transaction:
“My name is Mellisa and it is my pleasure to assist you in regards to the transaction between you and Rick Smith. We cannot credit your account until you send us the transfer details, but I am very happy to be assigned to tell you that the transaction is 100% secure and legitimate, we want to use this medium to tell you once again that the amount of $1,680.00 USD has been made to your account by Rick Smith.”
The email stated that if I had any concerns, I should express them by responding to the message. The email software would make the victim believe that such queries would go to [email protected], while in reality they would be directed to [email protected].
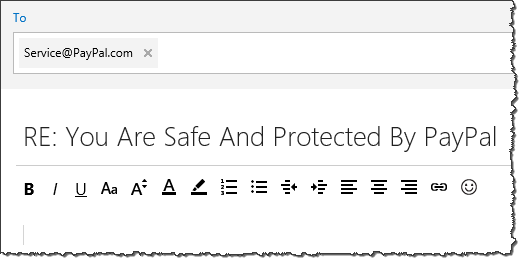
“Go to any Money Gram Outlet close to your home”
According to fake PayPal’s emails, I had to take one last step to complete the transaction: I had to send money via Money Gram to the buyer’s agent, who would be responsible for picking up the purchased item from my location. This step was explained in multiple emails, including the one from the supposed buyer, Rick Smith, which came from [email protected]:
“I want you to know that i added an extra fee of $680 to the total payment which i need you to help send to the agent coming for pick up and it needs to be sent via Money Gram as that’s the only way they can get it. I am sorry i should have informed you but i only got the urgent message from the pick up agent that they will need the funds before they can come to pick up when i was about making the payment. […] I also added $100 the Money Gram charges.”
One of the messages specified the name of the person who would pick up the money in Bangor, PA in the US. In the context of this scam, this person was acting as a money mule.
Though my emails to the fake PayPal account [email protected] went unanswered, the scammer did respond from [email protected] when I asked why he couldn’t pay the pick-up agent directly:
“There is no money gram here to make the transfer and I tried more that 4 times making the transfer online but they keep on rejecting my card.”
So, to receive payment for the item I was selling, I had to first send irrevocable funds to someone in Pennsylvania. In this case, the scammer requested funds via MoneyGram. Other variations of the scam that I’ve seen asked the victim to transfer funds using Western Union. Supposedly, the money I would receive via PayPal would reimburse me for that expense.
”Surf anonymously”
Curious whether I could gather any information about the scammer, I emailed him (or her) a link to a benign image that resided on my temporary web server. In my email message to the scammer I asked for help making sense of MoneyGram’s website and provided a URL to the screenshot. The scammer initially told me to visit MoneyGram in person, but after I threatened to give up on the transaction, I saw someone retrieving the image from my server:
GET /images/screenshot15.jpg HTTP/1.1
Host: 104.131.115.41
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/44.0.2403.157 Safari/537.36
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US,en;q=0.8If these headers are to be believed, the scammer was using an up-to-date version of Google Chrome on Windows 7. (The IP address 104.131.115.41 represents my web server.) The connection came from 208.31.49.29. This IP is on a /24 subnet assigned to Kaia Global Networks in the US, on the Sprint network according to Robtex. One Wikipedia page
I found indicated that this subnet hosted CyberGhost
VPN exit nodes. I downloaded this provider’s VPN client and was able to confirm that 208.31.49.29 is, indeed, one of the IPs associated with the paid version of the service.
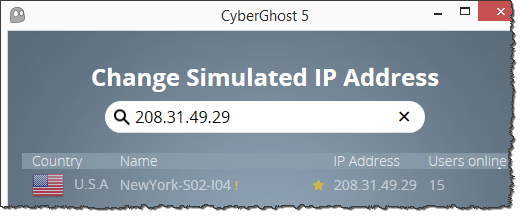
Alas, this scammer was careful to obscure his origins by tunneling through the this Romania-based VPN service, which is designed to “protect your online privacy, surf anonymously and access blocked or censored content.” According to my testing, CyberGhost’s VPN doesn’t modify browser headers, though the scammer could have tweaked them using other means.
When investigating another, very similarly-orchestrated scheme, I encountered a scammer who didn’t seem to use a VPN or a proxy when connecting to my web and DNS servers. That connection came from a network in Nigeria, which is one of the countries in the UTC +1000 time zone mentioned above. In that case, the scammer’s HTTP headers indicated that he was using a BlackBerry 10 device and even included the “msisdn” header that revealed his mobile phone number in Nigeria.
”The nature of my work”
I searched the web for the artifacts exhibited by the scammer in the interactions above to assess the scope of the malevolent activities. I found a few complaints associated with the two phone numbers. They dated to 2014, possibly because these VoIP numbers were misused for other shady machinations (1, 2, 3) at the time. I saw no mention of [email protected], though [email protected] was associated with several complaints that began in April 2014 and matched the pattern of this scam. At the time, “Rick Smith” was using other phone numbers, including 610-455-5663 and 914-268-3815.
When I pivoted my search on “Rick Smith,” I came across numerous reports (1, 2, 3, 4) from Craigslist sellers who were targeted in the manner described above. The phone numbers in these complaints were too numerous to list here. The reports mentioned other names and email addresses employed in the scam, including: [email protected], Anthony Smith, [email protected], Richard Johnson, [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], Frank Rick, [email protected], [email protected], [email protected], etc. The scammer’s pickup agentsmoney mules mentioned in the discussion forums above included: Levon Rivers, Columbus, OH 43227; David. Jacobo, Federal Way, WA 98003; Rob Frazier, Brooklyn, NY 11212; Terry Dunn, Lebanon, OH 45036; and Billy Ray Mayo, Livingston, LA 70754.
The earliest mention of the activities I observed and attributed to this scammer date to January 2012. At the time, the scammer used the email address [email protected]—the same address included in the body of the fake PayPal notification email that I received. The scammer’s target wrote that the scammer claimed to be on active duty in the military, using that excuse to explain why he could not speak on the phone or pick up the item in person. The scammer reportedly stated, “Am not available to talk through phone due to the nature of my work.”
This set of scams might be the work of a single miscreant. It’s also possible that a group of scammers is using a common toolkit to prey on Craigslist sellers. Regardless, I’m disheartened to see the volume of complaints associated with these activities. The person or people behind them seem to be operating with apparent impunity for years. Perhaps some of the details above can assist law enforcement with weaving these malicious actions into a pattern that helps identify the individual(s) responsible for them.
For more of my online scams research, take a look at Website Backup Company’s Misleading “Invoices” Suggest a Scam and Conversation With a Tech Support Scammer.