Protect Files From Malware With Windows Integrity Levels
Windows integrity levels can protect sensitive files from malware. Use the Chml tool to set a file to High integrity level with "no read up" policy enabled. Since malware typically runs at Medium level, it won't be able to read High-level protected files.
In an earlier post, I wrote about the use of the powerful Windows feature called mandatory integrity levels (MIC) to protect processes from spyware. In this follow-up note, I’d like to explore how integrity levels can offer additional safeguards for files of malware victims.
Windows Integrity Levels for Files
Windows integrity levels, such as Low, Medium, and High, take precedence over the traditional discretionary access controls, such as those that might prevent one user from accessing another user’s files. The idea of integrity levels is to restrict a less-trusted operating system objects to more-trusted objects.
To observe and manipulate some aspects of integrity level labels on the file system, Windows includes the icacls command-line tool. However, a tool called Chml—which is distributed for free by Mark Minasi—is a more powerful alternative.
Protecting Files from Malware Using Integrity Levels
Let’s say a user wishes to exercise extra care for protecting a particularly sensitive file. For our example, we’ll call it secret.txt:
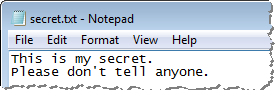
By default, a file created by a Windows user, even if the person is logged in with administrative privileges, is assigned the Medium integrity level:
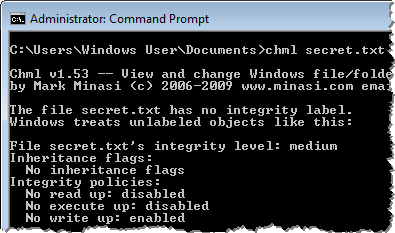
Integrity policies, shown by Chml, show that an object with a lower integrity level will be able to read and execute the file. That’s because “no read up” and “no execute up” policies are disabled by default. However, the object will be unable to write to the file, because the “no write up” policy is enabled.
To make it harder for malware to read the sensitive file, the user can set the integrity level of the file to High and also enable to “no read up” policy. Chml can do this with the parameters “-i:h” (sets the integrity level to high) and “-nr” (enabled the “no read up” policy).
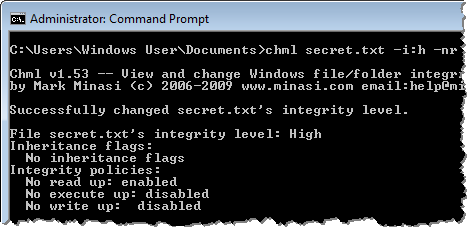
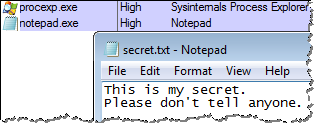
Since by default Windows launches processes under the Medium integrity level, user-mode malware running on the victim’s host will be prevented from accessing the file that was assigned the High integrity level. (You can look at integrity levels of processes using Process Explorer.)
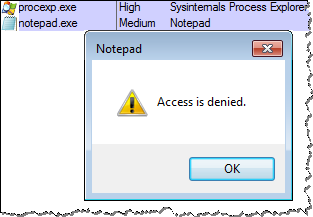
In the screenshot above, I used Notepad to simulate malware attempting to access the sensitive file
If the user wishes to access this file, he or she will need to run the program under the High integrity level. This can be accomplished by selecting “Run as administrator” when launching the program:
Using Windows integrity levels at the file system level provides another way of protecting victims from malware, in addition to the process-based integrity levels approach I discussed earlier. You can also use Windows integrity levels to limit capabilities of exploits.
If this topic interests you, consider the Combating Malware in the Enterprise course I co-authored, which discusses Windows integrity levels among numerous other relevant topics. Also, take a look at the Integrity Levels and DLL Injection write-up by Didier Stevens.