The ability to log keystrokes is a common feature in malicious programs. Endpoint security tools, including anti-virus software typically include anti-keylogger capabilities to combat this threat, but they don’t always work. Fortunately, Windows Vista, 7 and Server 2008 include a feature called mandatory integrity levels (MIL) that, if used correctly, can reduce the risk of users’ keystrokes being logged.
Keylogger in Action
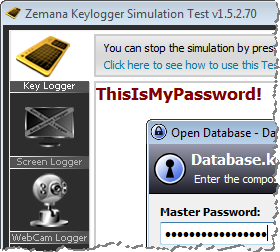
Malware authors can be very creative in coming up with approaches to spy on the victim’s activities. One way to experiment with such capabilities is to use non-malicious anti-spyware test programs that Zemana offers as a free download. For instance, the KeyLogger Test Program was able to capture the victim’s password even though the user had a modern Internet security suite installed:
Windows Integrity Levels for Processes
Microsoft incorporated integrity levels into Windows to restrict “the access permissions of applications that are running under the same user account.” These mandatory access controls assign trust labels, such as Low, Medium and High, to operating system objects, such as files and processes. The goal, according to Tony Bradley, is to:
"Ensure that only objects with an integrity level equal to or greater than the target object are allowed to interact with it. Essentially, if an object is less trustworthy, it is prohibited from acting on, or interacting with more trustworthy objects."
Integrity levels take precedence over traditional discretionary controls, which continue to exist in Windows at NTFS and registry levels.
Even when users are logged into Windows with administrative privileges, the processes they launch are assigned, by default, the Medium integrity level. You can view process’ integrity levels using Process Explorer. (To enable this column, go to View > Select Columns… > Integrity Level.)
In the keylogger example above, both the “spyware” process (keyboard.exe) and the “victim” process (KeePass.exe) were running under the same integrity level (Medium). This is party why the keylogger was able to capture the victim’s password.
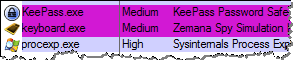
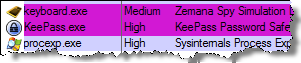
Note that Process Explorer (procexp.exe) was running under the High integrity level to have full visibility into all aspects of the system. To accomplish this, the user selected “Run as administrator” when launching its shortcut. This presented the user with the User Access Control confirmation screen, which is another feature for making it more difficult for malware to escalate its privileges (e.g., run with the High integrity level) without the user’s acknowledgement.
Using Windows Integrity Levels to Combat Spyware
Since Windows assigns the Medium integrity level to processes by default even if the user has administrative privileges, there’s a good chance that user-mode spyware will be running at the Medium integrity level. To make it harder for the malicious program to spy on the victim, users can launch the processes they need to protect from spyware under the High integrity level.
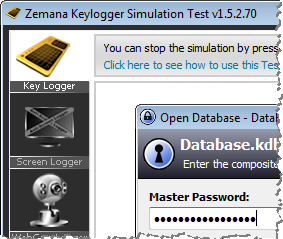
For instance, the user can select “Run as administrator” when launching KeePass. Process Explorer shows that in this case, the sensitive process runs under the High integrity level:
Because Windows doesn’t allow objects from a lower integrity level to access objects from a higher level, the keylogger is no longer able to capture the person’s keystrokes:
Windows integrity levels, when actually put to use, provide victims with some level of protection against malware. This mechanism is a powerful add-on to the traditional way of combating spyware by relying solely on anti-virus tools.
My recommendation to run certain processes under the High integrity level only applies to the tools that are not frequently at the risk of being targeted by exploits, such as as a password vault application. Programs that are at high risk of exploitation, such as web browsers, should be run with lower integrity levels to limit the capabilities of the exploit’s payload.
If this topic interests you, consider the Combating Malware in the Enterprise course I co-authored, which discusses Windows integrity levels among numerous other relevant topics. Also, take a look at the Integrity Levels and DLL Injection write-up by Didier Stevens and at chml and regil utilities by Mark Minasi.
Update: I also wrote a follow-up post that shows how to use Windows integrity levels to protect local files from malware.