The Adversarial Cycle of Computer Attacks and Defenses
The adversarial cycle has four phases: Attack (unfettered), Detect (forming response), Defense (attack rendered ineffective), and Mutate (attacker adapts). Defenders shorten Attack/Detect through faster detection and tighter lockdowns, and lengthen Defense/Mutate through deception and making analysis harder.
Understanding the dynamics of the actions taken by computer attackers and defenders is tricky, in part because attackers’ motivations and methods vary. Tao Stein, Erdong Chen and Karan Mangla defined a promising model, called the adversarial cycle, in the paper that describes the Facebook Immune System. The authors described the cycle using a diagram that I recreated below:
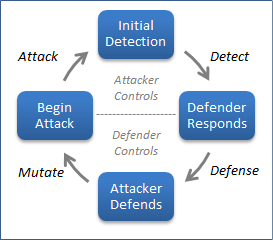
The authors explain that “during Attack, the attack has not yet been detected and is largely unfettered. During Detect, the attack has been detected but the system is forming a coherent response.” These aspects of the cycle are controlled by the attacker, because the defender isn’t yet in a position to disrupt the attack.
“During Defense, the attack has been rendered ineffective. The attacker may eventually detect this and begin Mutate to work around the defense mechanism.” In this phase of the cycle, the defender exerts control by restricting the attacker’s actions, until the attacker adjusts offensive tactics and reengages.
Representing the adversarial cycle in this manner helps not only understand the goals of both parties in the attack scenario, but also predict tactics. The authors explain that:
“The defender seeks to shorten Attack and Detect while lengthening Defense and Mutate. The attacker seeks the opposite, to shorten the bottom phases while lengthening Attack and Detect.”
Shortening the half of the cycle that attacker controls usually increases attacker’s costs.
Defenders can shorten the half of the cycle that attackers control by detecting attacks faster and by locking down the environment more tightly. Historically, defenders have been focusing on blocking attacks, without having sufficient detective capabilities.
Defenders can gain further advantage by lengthening the half of the cycle that they control by making it harder for the attacker to analyze the defensive actions that took place and bypass the controls. There are many ways of accomplishing this, including the use of deception in defensive practices.
By automating their activities, both parties in the adversarial cycle can gain an advantage. For instance, attackers might automate the Mutate action through the use of polymorphic malware or automated script obfuscation. Attackers might automate Defense by using intrusion prevention systems.
To learn how Facebook used the adversarial cycle model to automatically curtain malicious activities, be sure to read the Facebook Immune System paper.
Hand-picked related posts: