When investigating an incident that involved domain redirection and a suspected tech support scam, I recorded my interactions with the individual posing as a help desk technician and researched the background of this scheme. It was an educational exchange, to say the least. Here's what I learned about this person's and his employer's techniques and objectives. This tech support scheme was later investigated by the FTC and led to a settlement with the entities behind it, as outlined below.
You May Have Spyware
Tech support scammers used to call potential victims. Now that many people are aware of such skullduggery, the impostors found ways to persuade victims to be the ones to call the "help desk" company. I've seen this accomplished through the use of Twitter bots, typo squatting of domain names and redirection of expired domains.
In the incident I was investigating, the victim found himself on a scareware webpage that was hosted on fb.surveydonkeys.com (don't go there). The page was designed to convince the visitor that their system was infected, in the hopes of compelling the person to call the specified phone number to correct the problem:
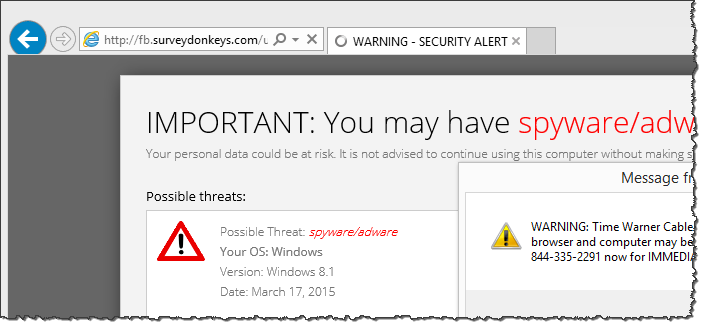
The page displayed the version of Windows running on the visitor's system, the current date and the name of the visitor's ISP. These pseudo-personal details were meant to add some legitimacy to the page. (You can view its source code on Pastebin.) The site also presented an alarming pop-up that warned:
"Your Internet Explorer browser and computer may be compromised by security threats. Call 844-335-2291 now for IMMEDIATE assistance."
Closing the pop-up window led to it opening again right away. As the result, the victim's browser was unusable. In addition, the site played the following urgent-sounding audio message on the person's speakers, imploring him to "call the number provided as soon as possible." You can listen to it here:
How May I Help You?
I used a "burner" phone to call 844-335-2291 to better understand the nature of the scheme. I was initially presented with a recorded voice menu, asking me to specify the type of problem I was experiencing. The recording sounded identical to the one I heard when investigating a Twitter-initiated variation of the scam earlier.
I was transferred to a human representative, who cheerfully answered, "Help desk. This is Steve speaking. How may I help you?" Steve sounded friendly, confident and spoke in non-accented, generic North American English. I could hear the background noise of people talking, indicating that he was in an office or call center environment. You can listen to our initial interactions here:
Steve explained that the reason I saw the security warning was because it was "a security feature that's built into the Operating System." He clarified, "If it's detecting something, it just directs you to give us a call." He also said that if for some reason he was unable connect to my computer, I could take my PC to a nearby Best Buy, Staples or Office Depot to have the issue investigated.
I suspect he mentioned these legitimate stores to indirectly associate his company with these trusted brands. He also wanted to build the foundation for explaining later the advantages of using his organization for remotely fixing my PC. Mentioning these alternatives also set a tone for the conversation: this was going to be a low-pressure, consultative sales pitch. You can listen to this part of our discussion here:
Diagnostic Tech 13
Steve patiently walked me through the steps necessary to give him access to my PC (I was using a laboratory system for the interactions). Steve directed me to go to www.support.me, which is a legitimate site that acts as the front-end for the non-malicious, popular remote support tool LogMeIn Rescue.
Following Steve's instructions, I installed the LogMeIn Rescue agent, which was digitally signed by LogMeIn. The tool informed me that "Diagnostic Tech 13" was requesting he ability to remotely control my system. The tool's pop-up indicated that the technician was from "Help Desk National." I clicked OK:
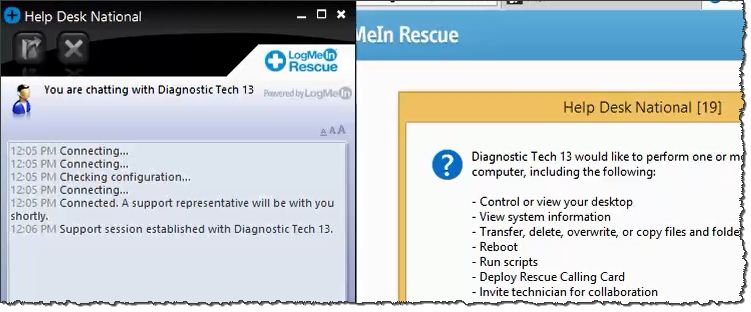
Tools such as LogMeIn Rescue are useful in both authorized and malicious remote access scenarios. Since this tool is legitimate, software from a respectable company, it's unlikely to be blocked by victims' malware defenses. Also, the remote party is able to use the tool to control the system without establishing direct network connections to the PC, because the connections are sent through LogMeIn servers.
We're With the Operating System
I asked Steve why my system instructed me to call his organization when I was browsing earlier. "Are you with Microsoft?" I prompted. Steve was careful not to answer my question directly:
"That's a security feature that's built into the Operating System," he explained. "If it's detecting something, yeah, it directs you to give us a call. If it's detecting something either attacking the Operating System or potentially attacking the Operating System, it directs you to give us a call now."
"Are you with Microsoft?" I asked again.
"Right, this is help desk. It's for Windows Vista, 7, 8 and 8.1," he responded.
"I see, so did I buy the computer from you, is that why it's calling your help desk?" I pressed.
"No, no. It's because you're using the Windows Operating System. As a matter of fact, you're using 8.1. That's why."
You can listen to this slightly surreal exchange here:
I revisited the topic later in our conversation, asking, "I'm a bit confused um... did I call Dell? I'm not sure. Or Microsoft?"
"No, this is help desk. Yeah, this is for Windows Vista, 7, 8 and 8.1," Steve told me. "So this is with the Operating System, not Dell. Dell is the manufacturer of your computer."
"Aha, so you're the guys who made the Operating System?" I offered.
"Right, we're with the Operating System," he confirmed.
"I see."
"That's Windows. Windows Vista, 7, 8 and 8.1," he repeated.
I suspect Steve was trained to always respond with the same set of phrases when asked about the organization he represented. "This is help desk" and "Windows Vista, 7, 8 and 8.1," he kept repeating. After a while, even the most curious of callers will give up asking even if the answers don't fully make sense, as long as the answers are delivered consistently and with confidence.
You can hear this part of our discussion here:
It's a Microsoft Silver Product
Consistent with the consultative style of our conversation, Steve took the time to educate me about what "Microsoft recommends for maintenance and prevention" of computer problems:
"There are two things. Write them down if you need to. That way you don't forget."
"OK," I said.
"Allright, number one—and Microsoft is very adamant about number one—because they do not recommend you even connect to the Internet anymore unless you have the right type of protection on your computer. For protection what's recommended now, it's called STOPzilla. It's a Microsoft Silver product. It's designed to protect against both virus and malware detection on your computer. Does that make sense?"
"Yeah, you said its called STOPzilla?" I asked.
"Right, STOPzilla," Steve confirmed. "So S-T-O-P and then Z as in zebra, I-L-L-A. STOPzilla."
"So Microsoft makes it?"
"Yeah, it's a Microsoft Silver product," he said.
I have not heard of STOPzilla before. As far as I can tell, it is a one of the lesser-known antivirus tools. I don't have direct experience with it, but I saw a number of complaints about the product on the web. Let's just say that this would not be my go-to choice for malware protection.
Steve used the passive voice when stating that STOPzilla is "recommended," without directly stating that this is the product that Microsoft recommends. However, that was implied in his explanation. You can listen to Steve talking about STOPzilla here:
I asked Steve what he meant when he said that STOPzilla was a Silver Product. His response was, "It's a Microsoft Silver product." This was probably a part of his training, one of the keywords he was instructed to use in association with STOPzilla.
"Is there a Gold that's like better than Silver?" I inquired.
"Yeah, Microsoft Silver is for like regular consumers," he seemed to improvise. "Microsoft Gold is more for like... uh... most companies. People who are like using T1s and servers and things like that. Because the Gold products normally have 24/7 protection, where there's somebody that's essentially monitoring the system, physically."
The phrase "Microsoft Silver product" was designed to add legitimacy to his advice, even though this statement doesn't quite make sense. Steve was probably referring to the claim I saw later on the STOPzilla website, which stated that they enjoyed the Silver Certified Partner status with Microsoft.
They All Do Tune-Ups
Steve continued to educate me about Microsoft's recommendations for maintaining a healthy PC:
"The other thing that's recommended—make sure you write this down too—other than number one, Microsoft says that you need to make sure that you're getting the computer tuned up by a certified technician at least twice a year," he explained.
"I see. Are you a certified technician?" I asked.
"Right, yeah. As a matter of fact, I'm gonna go over that now," Steve continued. "Because places where you can get tune-ups done would be Best Buy, Staples, Office Depot, OfficeMax, CompUSA, or if you want it done remotely, we do have a help desk also. Any of those places I just mentioned, they all use Microsoft certified technicians and they all do tune-ups."
His claim that a certified tech needs to perform biannual maintenance on a PC was designed to get the victim thinking about the eventual need to pay someone to get this work done. In saying this, Steve was continuing to build the case, in a low-pressure way, that his firm is the best candidate to perform the work. The caller is not quite ready to hear the payment request, but we're gradually getting there.
You can hear this part of our exchange here:
46 Processes
Steve explained that he will look at my system's Task Manager. "Normal usage on a healthy computer should be as close to 40 processes as possible," he said. "Because if that number is higher than that, that can indicate that things have attached themselves to your computer that are starting to affect your Windows functionality. So we'll both know what's happening to your computer momentarily. I'm going to pull that up right now."
He attempted to pull up Task Manager and was surprised to discover that I replaced it with Process Hacker, which I prefer to use in my lab. Steve recovered quickly and pointed out that I had 46 processes running!
"Take a look down here. See where it says processes?" he prompted. "That's the problem. That's why you're getting the message popping-up. You see right here at the bottom?"
"46 processes? So that's 6 more than normal?" I asked.
"Yes, right. What this means is, your computer is doing 46 different things at the moment," he explained.
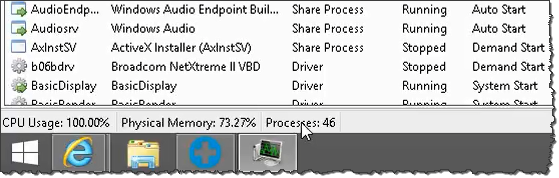
Steve continued, "Wow, that would definitely indicate why you're getting the message." This was in reference to the fake security warnings that prompted me to call. He assured me, "Once you get the computer repaired, and you get the proper protection installed into the computer, that will help you prevent that problem in the future." (I suspect the follow-up conversation would involve a sales pitch for the above-mentioned anti-malware product like STOPzilla.)
Watching out for my interests, Steve said, "You need to make sure that once the computer is repaired though, just do what Microsoft says, just make sure you're getting it tuned up at least twice a year. 'cause problems like this, these are maintenance issues. Technicians, they'll find this way before you'll get a message to contact us at help desk."
You can listen to these interactions here:
Are You 55 Years or Older?
Steve explained that if I took my computer for repair to a local store, I "would lose the PC for about 5-7 business days and for that type of repair it's normally between 300 and 350 dollars to do the work." He continued, "Or, you could do same-day-service, it's not a problem. The only thing is, what you have here, 'cause you have a lot of processes, are you able to stay off the computer for a couple of hours right now?"
"What's involved in getting this serviced?" I asked. "Should I just take it to a local Best Buy, maybe? Maybe on a weekend?"
"Well, remote repair works a bit different than in-store repair works," he said. "Let me ask you, are you 55 years or older or military or veteran?"
"Uh... why does it matter?" I prompted.
"Because it's a different repair program if you're any of those 3."
"So I don't qualify for repair if I'm under?"
"No, I said, if you're any of those 3, then remote repair for senior citizens, it's a different discount program. Regular remote repair is $250. If you're a senior citizen, though, it's $199."
At last, we got to the point. Now that Steve's examination of my computer "confirmed" that my system was infected, he was willing to provide me with a fast "remote repair" service for a fee that was less than what I'd reportedly pay the local stores.
You can hear this part of the conversation here:
For Your Protection
"Do I pay after the work is done?" I inquired. "No," said Steve. "I'm gonna set that up now. As a matter of fact, you're gonna fill out that information on your screen. That's for your protection. 'Cause we don't... we used to do that a couple of years ago, but now you fill that out on your own."
He proceeded to confirm my phone number, which he obtained via caller ID. He said it was necessary, so that the technicians knew where to reach me "once they're done with the repair and installation." Steve insisted that I give him my email address. When I said that I wasn't sure what it was, he helped me create a brand new Gmail account, so I could complete the transaction. He was quite patient.
Next, Steve pulled up a web page that displayed the form where he wanted me to type my credit card and contact information. He brought up the site in an unusual way, avoiding the normal browser. Instead, he used Windows' HTML Help application to visit the URL that he quickly copied and pasted via the clipboard. This approach precluded me from seeing the URL and also prevented the URL from being saved in the browser history.
I was able to recover the full URL using a bit of memory forensics afterwards. (Later I noticed that Steve left it in the system's clipboard.) Here is what it was, but don't go there:
https: //ssl.clickbank.net/order/orderform.html?vvvv=68656c70646e&item=1pcAV250&affi=dougmarsha&vtid=JeffreyRaulerson&order.shipTo.fullName=Jake Robinson &order.shipTo.email=jakerobinson1956@gmail.com&order.shipTo.phoneNumber=2674221374&order.shipTo.countryId=1&order.shipTo.zip=10078&order.paymentInfo.creditCardNumber=&order.paymentInfo.expireMonth=&order.paymentInfo.expireYear=2013&order.paymentInfo.cvv=&vvar=dnis%3D8558382870%26ani%3D2674221374%26affiliatepayout%3D0.00
As you can see in the URL, Steve pre-filled some fields based on the data I provided to him, including my name ("Jake Robinson"), zip code ("10078"), phone number ("2674221374") and freshly-created email address ("jakerobinson1956@gmail.com").
Steve's URL also included the Affiliate ID (affi) of "dougmarsha" and the Vendor ClickBank Tracking ID (vtid) of "Jeffrey Raulerson." The resulting payment form looked like this:
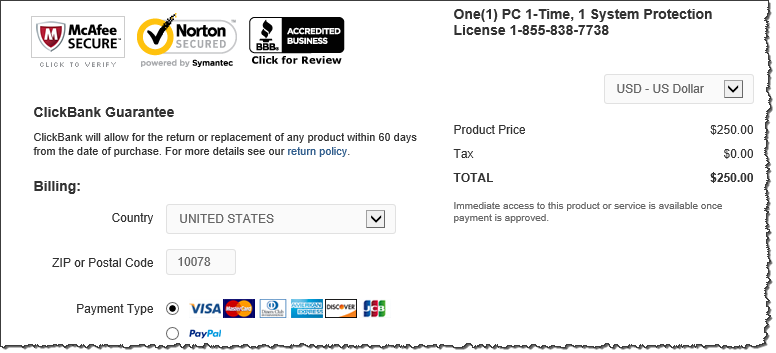
ClickBank describes itself as "the leader in performance marketing" according to its website, which also states, "Make money online with our affiliate marketing program and online marketplace for product creators." In the case of this tech support scheme, ClickBank was acting as the payment gateway, allowing Help Desk National to charge its victimscustomers.
At this point in our conversation, I told Steve (or was that actually Jeffrey?) that I felt uncomfortable paying until the repair work was completed. He replied, "I cannot have the technicians do repairs until it's paid for." When I said I prefer to take the PC to a local Best Buy. "No problem," he responded and reminded me that local stores will take 5-7 business days to do the work and will charge $300-$350. Once he realized that I wasn't interested in his firm's services, he hung up and disconnected from the PC.
15% to 20% Commission
How are help desk reps such as Steve/Jeffrey hired? Following a tip from a reader, I located a Craigslist ad that was posted on the South Florida section of the site. It was seeking tech support personnel for an inbound call center in the Boynton Beach area. The posting asked job candidates to "call Harold for phone interview" at 954-274-2466.
The address of the office specified in the ad was 2240 W Woolbright Rd, Boynton Beach, FL. This corresponds to a multi-tenant office building, though it's possible that this is a fake address. Here's the building's photo I obtained from Google Street View:

The ad requested the candidates to have sales, customer service and call center experience and promised 15% to 20% commission. I came across another version of the ad, which promised the lucrative compensation of "300 Base and Plus Commission."
Visa Technical Glitch
I heard from one person who was persuaded by Help Desk National's fake security warnings and sales tactics to pay for their service. She told me that the technician worked on her PC for 10-15 minutes after she paid $202 to fix the "problem." (Being over 70 years old and living on Social Security, she qualified for a senior citizen's discount.)
The purchase order emailed to her by ClickBank showed www.helpdesknational.com as the vendor support website, and included another website—fastfix123.com—as the vendor homepage. Perhaps Help Desk National used that URL for earlier schemes, or perhaps it was preparing to switch to this domain for future interactions.

Surprisingly, the fee for this transaction was refunded by ClickBank several days later, even though she did not yet have the opportunity to request the reimbursement herself. According to ClickBank, they decided to refund the money because of the feedback regarding such transactions that they received from other customers:
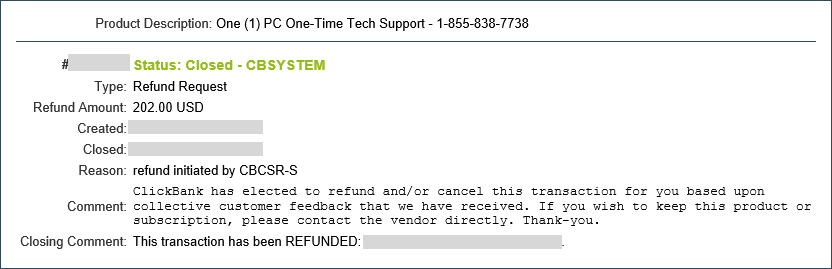
ClickBank has the incentive to cut off fraudulent vendors or reverse suspicious transactions before the affected customers complain to their card issuers. Visa and MasterCard and the associated banks will raise ClickBank's transaction fees if they receive too many legitimate complaints. I suspect ClickBank took this action after deeming Help Desk National's actions fraudulent.
Perhaps even more interestingly, Help Desk National reached out to the person who received the refund, attempting to persuade her to pay again for the rendered services in lieu of the refund. The message blamed the refund on a "Visa technical glitch:"
"We are writing to inform you of a recent refund which was erroneously applied to your Visa credit card on April **, 2015. Our firm, Help Desk National, between the dates of March ****, had been engaged directly by you to help optimize your computer performance and possibly install software to eliminate the potential for future virus or popup attacks. Our technicians were engaged and subsequently repaired your computer, freeing it up from any possible future attacks. In exchange for this work your card was charged $202.00 .
On April ** you will notice that a refund appeared on your visa statement from CLKBANK*855 838 7738 in the amount of $202.00 . This error was the direct result of a Visa technical glitch which has since been corrected. At this point our company has not been paid for the work that it has successfully performed on your computer."
The email was seeking approval "to reprocess the original transaction" and asked the recipient to contact the "Billing departme nt, by phone at (855) 838-7738 ext. 5." The email was signed by Phil Dunleavey, Retention Manager. The audacity of this communication is quite impressive.
Was This a Scam?
Was Steve/Jeffrey leading me towards a fraudulent transaction? I observed no exploits and no malware. The organization (Help Desk National?) that he represented might claim that they were providing a valuable service by educating people for free and repairing their PCs in exchange for a service free. And yet, most aspects of this scheme are questionable at best and involve misleading statements and half-truths.
The potential victim's experience began with a web page that was designed to make its visitors think that their PCs were infected. Yet, the page carefully qualified its claims with words such as "may" be infected and "could" be at risk. Regardless, many non-technical people would not pick up such nuances and would be convinced by the text and graphics that their systems were in need of repair.
The tech who answered the call associated himself with trusted brands, while avoiding saying that his firm had a direct relationship with Microsoft. His statements regarding Microsoft's advice were worded in such a way that what some might call a lie, he would call a misunderstanding. He could claim that he was attempting to assist a person who suspected that his system was infected. He could also claim that he analyzed the system, with the person's permission, and noticed indicators that repair was needed. Sure, his indicators were based on meaningless and misleading information, but the tech could claim incompetence instead of malicious intent.
The tech wanted to take money from the caller in exchange for cleaning up the PC. He could claim that he was charging for a legitimate service. I don't know what would happen once the person paid the fee, and therefore cannot determine whether the "repair" would involve meaningful work or whether it would be a sham. (Somehow, I doubt the person would receive high-quality services.)
The tech also set the stage for selling anti-malware software to the caller, such as STOPzilla, perhaps in a follow-up transaction. Such tools doesn't seem malicious, but they are not necessarily very effective. The web site that seems to belong to Help Desk National (helpdesknational.com) sells such products at prices much higher than what one would pay when purchasing the software directly from its developer.
Is that fraud or just capitalism? While the individual elements of the tech support incident could be defended as not being directly fraudulent, taken together, they form a scheme that is unethical and scammy. Moreover, in response to this article Benjamin Wright pointed out that "in the US, federal and state law prohibit deceptive and unfair trade practices. See for example the Federal Trade Commission Act." One might argue that the scheme above is both deceptive and unfair.
I hope this post helps potential victims avoid getting caught in the net that was masterfully woven by organizations and individuals involved in such tech support machinations.
Business Pivot Several Months Later?
The article above was originally published in March 2015. In December 2015 I spoke with a Sales Manager working at Help Desk National, after reaching out to him on LinkedIn. He asked me not to identify him by name in this write-up.
The Sales Manager informed me that the company no longer uses affiliate ad networks to generate inbound calls. Instead, he said they now rely on organic search results to reach prospective customers. However, I spoke with another individual who said he worked at the firm in the recent months and that he witnessed the use of scareware ads to persuade prospects to call for tech support.
The Sales Manager disagreed and said that the company is now "in a completely different space" than before and that they are focused on helping customers. He explained that their technicians now use the free tool Webroot System Analyzer to assess the state of callers' systems in a more reliable manner, instead of looking at process listing. He also said that the firm still resells anti-malware software, but refused to specify which product it is offering now.
Help Desk National Shut Down, Settlement Reached
More than a year after this article's initial publication, "Florida's Attorney General has obtained a temporary injunction against Boynton Beach tech support company Big Dog Solutions, which also does business as Help Desk National and Help Desk Global," according to SunSentinel. The article further stated that a "permanent injunction, filed June 28 [2016] in U.S. District Court in Northern Illinois, alleges violations of U.S. telemarketing and e-commerce laws, as well as state law prohibiting unfair and deceptive practices." On or around that date, Help Desk National's website went offline. A copy of the FTC and Florida's Attorney General filing associated with these activities is available on-line.
In May 2017, the FTC announced that it achieved settlement with "two massive tech support operations that they had previously sued for bilking consumers out of millions of dollars," which included Big Dog Solutions and related entities.
In January 2018, the FTC announced that was "mailing refund checks totaling more than $668,000 to victims of a tech support scam that claimed to be associated with major tech companies to trick people into buying tech support services," mentioning "Big Dog Solutions LLC, also doing business as Help Desk National and Help Desk Global, and related defendants" in the announcement.
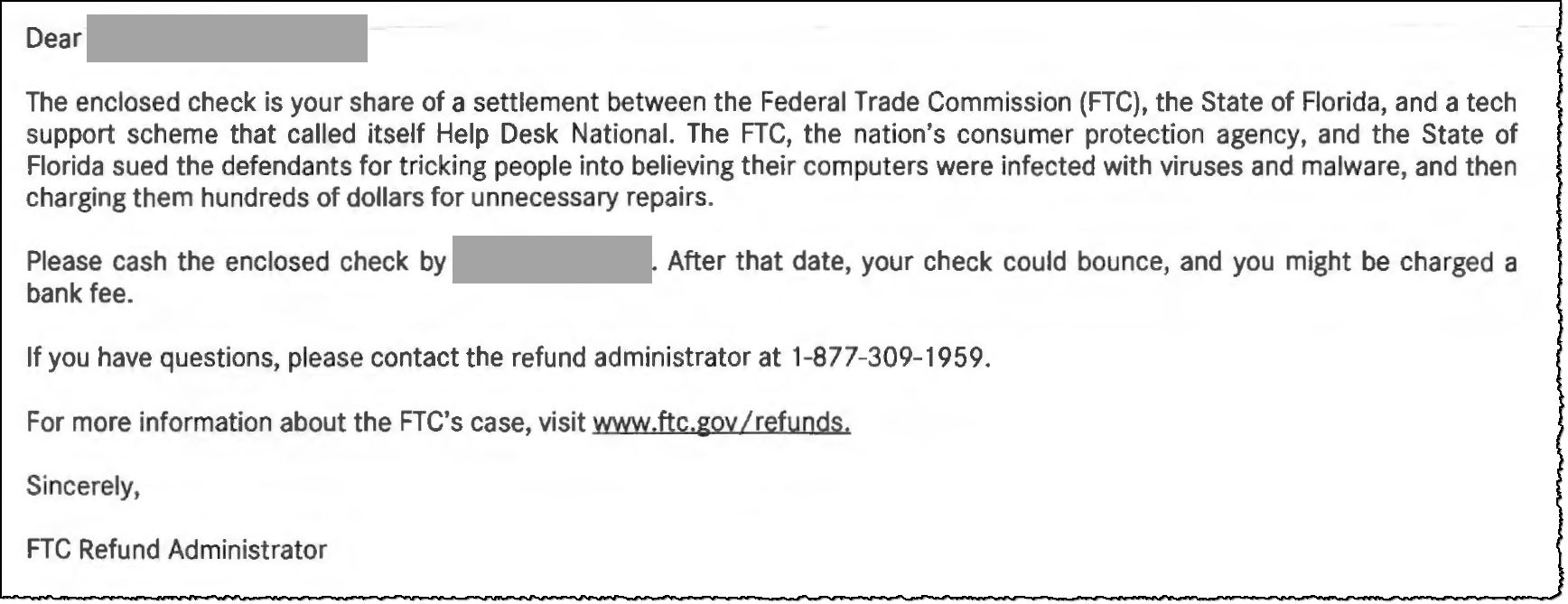
As the result of the actions by the FTC and the State of Florida, the individuals affected by the scheme received the following (legitimate) letter and the accompanying check from the refund administrator. It stated, "The enclosed check is your share of a settlement between the Federal Trade Commission (FTC), the State of Florida, and a tech support scheme that called itself Help Desk National. The FTC, the nation's consumer protection agency, and the State of Florida sued the defendants for tricking people into believing their computers were infected with viruses and malware, and then charging them hundreds of dollars for unnecessary repairs."