The the most popular method for distributing malware for mobile devices has been grounded in social engineering. We haven’t seen many exploits pursuing vulnerabilities to infect mobile devices because it’s simpler and often more reliable to persuade the user to install a malicious program. Let’s take a look at how such attacks have occurred and why they’ve been so effective.
Malicious Apps that Look Legitimate
The most common social engineering approach employed by mobile device malware involves masquerading as a legitimate application. This technique, which spreads malware in the form of trojan programs, has been employed by malicious software on other platforms for a long time.
This has been a major issue on Android, which offers few barriers to listing a program on its various app marketplaces. For instance, Google removed over 50 malicious apps from Android Market in Spring 2011 that seemed turned out to be variants of the DroidDream trojan, but looked like legitimate applications and had names like Super Guitar Solo.
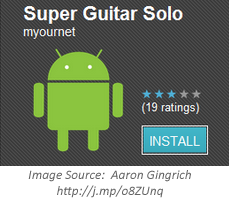
The persuasion mechanism of this approach to distributing malware is simple: Create or customize an app that a user might want to download and list it in the app store/marketplace. Then wait for victims to install the malicious program. Examples of trojan mobile apps for other platforms include malicious versions of Terdial for Windows Mobile and Mosquito for Symbian games.
Advice: Don’t install apps from untrusted developers. Relying on the app’s ratings may be insufficient, because many users might be enjoying the app’s features without realizing that it contains hidden functionality.
Illegitimate Sources of Mobile Apps
The efforts to persuade the victim to install GGTracker malware on Android began with an ad displayed within a legitimate app running on the phone. According to Lookout, the ad directed the person to a website that claimed to analyze the phone’s battery.
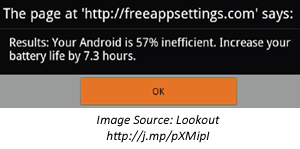
After clicking OK, the victim would be redirected to a page that looked like Android Market, which attempted to convince the user to install a “Battery Saver” app that turned out to be malicious.

By default, Android is usually configured to disallow the installation of applications that originate from a source other than Android Market. In anticipation of this, the malicious app advised the user that:
"Due to the power savings this application produces, its only available outside of the Android Marketplace. You might need to unblock the install by updating your Settings."
Since Apple exercises a much tighter control over its App Store, it’s harder for the end-user to install an app that comes from another source. Moreover, all user-installed apps have to be signed by Apple. this is probably why we haven’t seen such incidents affecting iOS today. To install an unsigned and untrusted app, the iOS user would have to be running a jailbroken iPhone or iPad device. It may be possible for a malware developer to distribute an app outside of App Store using the iOS Developer Enterprise Program; however, Apple still exercises some control over the apps distributed in this “Ad-Hoc" manner.
Advice: Don’t enable support for installing apps from sources other than the phone’s manufacturer. If jailbreaking your mobile device, understand the risk involved in installing apps from potentially-untrusted third parties.
Installation Request from the Victim’s PC
In the case of ZeuS malware variants that target mobile devices, persuasion originates from the victim’s PC. When the person visits a banking site from an infected computer, he is prompted to “download an authentication or security component onto their mobile device in order to complete the login process” according to Trusteer. In one case, as reported by Kaspersky Lab, the message attempted to trick the victim into installing a fake version of the Trusteer Rapport app for Android.
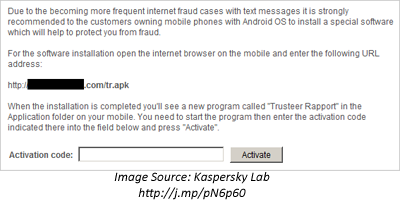
Since the victim was under the impression that the request to install the program came from a bank (a trusted entity) and because the request was made in the name of security, the person was likely to drop his guard and install the malicious program on the phone.
Advice: Be cautious of requests to install a mobile device app, regardless of the venue through which the request arrives.
Wrapping it Up
As we’ve seen, authors and distributors of mobile device malware have been effective at using social engineering techniques to trick victims into installing malware. Though there are some steps people can take to avoid being manipulated in this manner, the reality is that withstanding well-crafted social engineering campaigns is incredible hard. This is especially applicable to mobile devices, where visual indicators that may help users understand the context of their actions are often lacking.
Related:
- The Changing Landscape of Malware for Mobile Devices
- Incorporating Mobile Devices into Enterprise Security