An Example of SMS Text Phishing
SMS phishing ('smishing') messages impersonate carriers like Verizon to direct victims to credential-harvesting websites using spoofed sender numbers and lookalike domains. Mobile users are especially vulnerable because phones lack the visual security indicators present on desktop browsers.
Phishing—a technique grounded in social engineering—remains an effective way for attackers to trick people into giving up sensitive information. Potential victims can be contacted by email, fax, phone calls and SMS text messages. Below is an example of such a scam sent through SMS—a practice sometimes called smishing.
In this case, the recipient is requested to visit update.vtext02.net to update account information, supposedly so that he or she can continue using Verizon services.

The phone number of the SMS message’s sender was most likely spoofed.
The malicious domain vtext02.net appears to have been shut down by its registrar several hours after the phishing text message was received. When it was still active, the victim visiting the link on the SMS message would have seen the following page that mimicked the Verizon Wireless website:
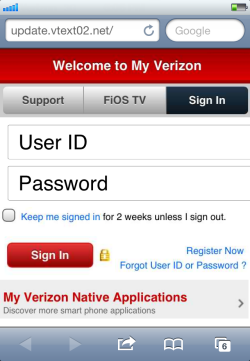
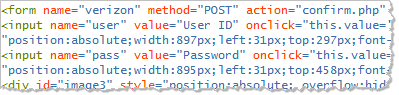
All elements of this page were unclickable images with the exception of the form that prompted the victim for his or her Verizon account credentials. The “Sign In” button would submit the data to the phisher’s server-side confirm.php script. Here’s an excerpt from the page’s HTML code:
A similar incident was publicly described by another person about a month earlier. In that case, the sender was being directed to another malicious URL. The phishing SMS message stated “V.erizon.wireless.update. Please click on http:// verizon.vtext-1.com and proceed.” (Don’t go there.)
Mobile phone users are especially vulnerable to social engineering scams. One of the reasons for this, as pointed out by ESET’s Randy Abrams, is that “virtually none of the visual indicators that help even a moderately savvy novice computer user make informed decision are present on mobile devices.”
Russ Klanke documented the steps for reporting a suspicious SMS message to the GSMA Spam Reporting Service by sending a text to short code 7726 (SPAM).
Hand-picked related articles: