Computer attackers exhibit an increased interest in contents of email messages. The intruder can gain access to the messages by directly querying the victim’s mail store or by accessing the corporate centralized message store. There’s one more attack vector to consider: third-party “cloud” add-ons and services that have been granted access to email and other communication data.
Options for “Cloud” Email Search Add-Ons and Services
I’m talking about the increasingly-popular email search tools that make it easier for users to locate, analyze and make use of messages and contacts. The choices include:
- Greplin “indexes the information you create on different websites (like Gmail, Twitter and Facebook).”
- Xobni for Gmail “creates rich profiles for every person you’ve ever communicated with” and includes “info from Facebook, Twitter and LinkedIn.”
- Gist indexes “your contacts across all your inboxes, social networks, and lists assembled in one place.”
- Backupify offers “archiving, search and restore service for the most popular online services including Google Apps, Facebook, Twitter and more.”
- CloudMagic “provides search across multiple services, viz. Gmail, Google Apps Email, Google Docs & Contacts.”
Granting Access to Email Data
To make use of these tools, the user needs to authorize them to access the desired email and social networking accounts. For instance, TechCrunch described the process for getting started with Greplin:
"A typical user may sign up and start off by authorizing Greplin to index Facebook, Twitter and Gmail, for example. Greplin then grabs everything in those services – all your Facebook messages and updates, all your Twitter updates and DMs, all your Gmail messages back and forth, etc. , and lets you search them."
From an attacker’s perspective, the vendors’ systems used to store and process email and other communications form an attractive target: By compromising the systems used for storing content and/or its indices, the intruder can gain access to a treasure trove of valuable data.
Some people recognize the risk of granting these tools access to their data and decide to use the tools regardless. For instance, I came across a blog posting by Josh Fraser in which he wrote:
"There’s an obvious concern about the security aspect of using Greplin since they have access to all my content and are storing the indexes in the cloud. For me, the value they provide is big enough that I’m willing to take the risk and I’m not one to hand over the keys to my data easily!"
Josh performed the risk vs. benefit analysis and decided to accept the risk. Good. However, I wonder how many people install such tools without given a second thought to data security implications?
How Do These Services Secure Users’ Data?
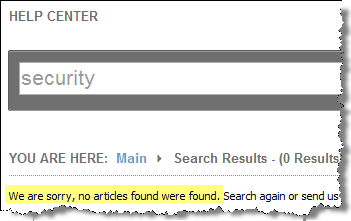
I’ve been unable to find much information about the security measures that the vendors implement to protect users’ data beyond the vague language typically found in privacy policies. For instance, searching Greplin’s on-line help system for “security” gave me zero hits:
Backupify simply says “Any information we have about you is stored with strong encryption.” What does that mean? (For instance, how is key management handled?)
Gist does a better job describing some aspects of its security, clarifying that “Gist also has the ability to upload your email contents to Gist” and outlining other data that the service has access to. However, there are few details regarding the actual security controls that might be in place.
CloudMagic stands out from many other tools in this category by storing the email index on the user’s local host and, therefore, addressing many of the security issues that the other vendors need to consider. According to the company, it “never exchanges account’s authentication details or its content with any third party servers including ours.”
Take-Aways
Email search add-ons and services provide valuable features that users want. I’m excited to see the innovation that the vendors exhibit by helping people make use of the ever-growing pile of email and other communication data. At the same time, I worry that the vendors aren’t paying sufficient attention to security of the highly-valuable data they process and store. I also worry that users of such tools adopt them without considering the risks.
As the strategies employed by computer attackers increasingly exhibit market segmentation attributes, the threats evolve toward more focused, nimble tactics. One aspect of this trend is the attackers’ interest in email contents, which is why it’s so important to pay attention to how access to email and other communications is controlled—not only locally, but also through the use of “cloud” search add-ons and services.