The gist of how regular people differ from security professionals in their perspectives on activities that affect information security:
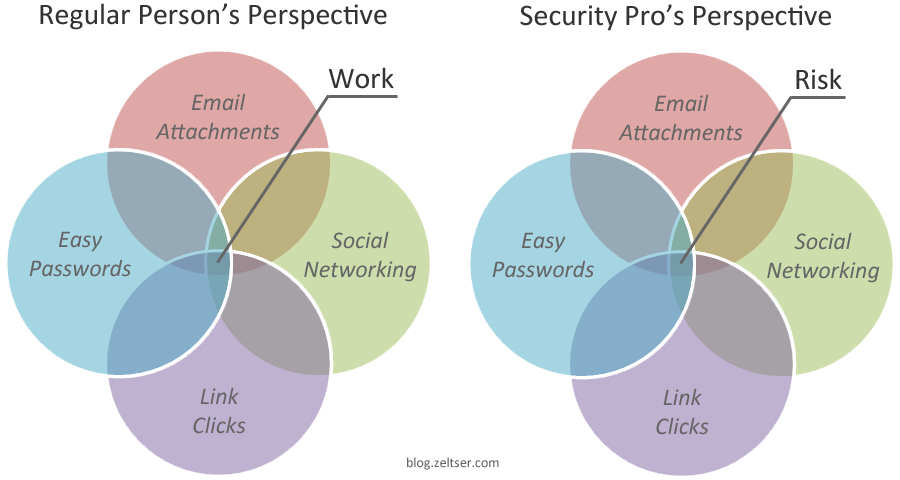
My conclusion: While there's the need to control the actions that might put the organization’s data and compliance at risk, a security program should be designed with the assumption that people will find ways around security measures to get work done in a way that suits them best.
Updated February 6, 2015
Lenny Zeltser About the Author
I transform ideas into outcomes, building on my 25 years of experience in cybersecurity. As the CISO at Axonius, I lead the security program to earn customers' trust. I'm also a Faculty Fellow at SANS Institute, where I author and deliver training for incident responders. The variety of cybersecurity roles I've held, and the expertise I’ve accumulated allow me to create practical solutions that drive business growth.
Learn more
