How Information Security Professionals Are Different
The gist of how regular people differ from security professionals in their perspectives on activities that affect information security:
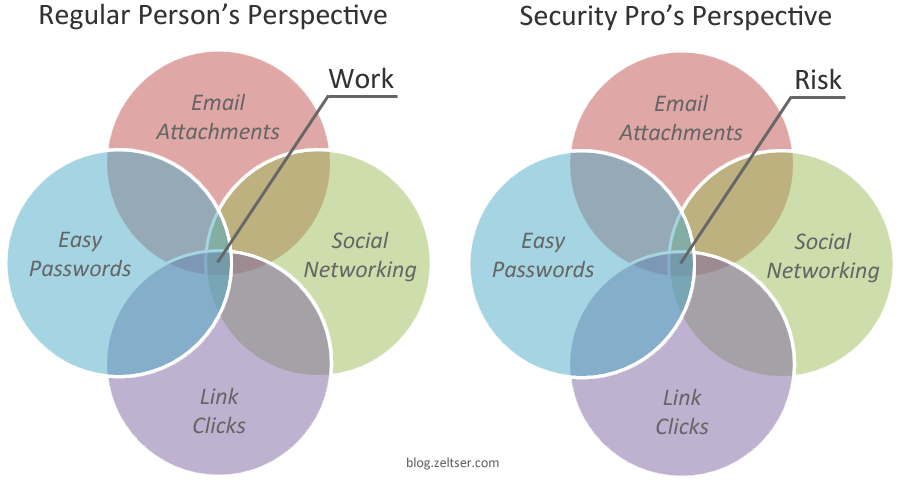
My conclusion: While there’s the need to control the actions that might put the organization’s data and compliance at risk, a security program should be designed with the assumption that people will find ways around security measures to get work done in a way that suits them best.