3 Free NirSoft Tools for Malware Analysis
Three NirSoft utilities complement Process Monitor for behavioral malware analysis: ProcessActivityView shows file system access with bytes read/written, RegFromApp monitors registry changes, and ProcessThreadsView displays thread details including stack strings. They're quick "second opinion" tools.
Nir Sofer makes a number of Windows utilities, which he distributes for free on the NirSoft website. This post takes a quick look at 3 of his tools—ProcessActivityView , RegFromApp and ProcessThreadsView—which can be handy when analyzing malware from a behavioral perspective. These programs can be a useful supplement to Microsoft’s Process Monitor and Process Explorer tools.
ProcessActivitView
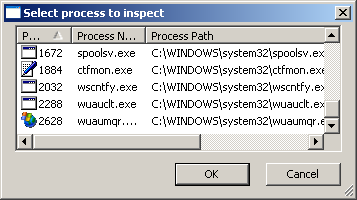
ProcessActivityView delineates which files and folders the designated process attempts to access. It allows you to begin tracing an existing process by letting use select from an active process listing:
**
**
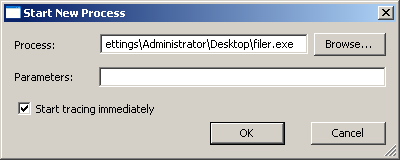
The tool also allow you to start a new process and begin tracing it immediately:
**
**
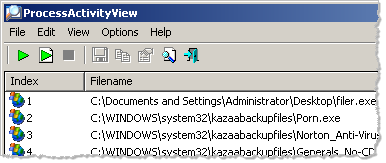
ProcessActivityView displays a real-time log of the file system activity associated with the monitored process. In addition to displaying the file path, the tool displays tracks how many times the file was opened, how many bytes were read and written, etc. It also displays the DLL that made the last open-file call:
RegFromApp
RegFromApp monitors registry activities of the designated process, displaying a log file of registry changes. This can be a quick way to observe how a malicious program attempts to change the registry:
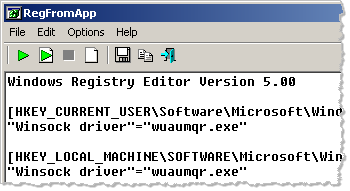
Like with ProcessActivityView, you can point RegFromApp to an existing process or tell it to launch the specified executable and begin tracing it immediately.
ProcessThreadsView
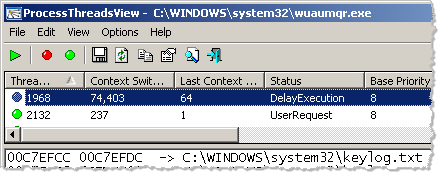
ProcessThreadsView is designed similarly to ProcessActivityView and RegFromApp, letting you monitor existing processes or trace new ones. When active, this tool displays information about the threads of the designated process, including strings found on the stack of each thread and much more:
Good Supplement to Other Tools
ProcessActivityView, RegFromApp and ProcessThreadsView are quick and easy to use to give you some visibility into registry and file system capabilities of malicious programs. However, they generally aren’t as comprehensive as Process Monitor, to some extent, Process Explorer. I consider them “second opinion” tools, and like having them as part of my malware analysis toolkit.
Hand-picked related items:
- Process Monitor Filters for Malware Analysis and Forensics
- Using Netsh for Easier Network Setup in a Malware Lab
- Process Hacker as an Alternative to Process Explorer
Just so you know, I teach the malware analysis course at SANS Institute.