Process Monitor Filters for Malware Analysis and Forensics
Process Monitor captures enormous amounts of data that can overwhelm analysts. Custom filters help by hiding boring entries or highlighting interesting events. Downloadable filter sets look for activities associated with malware: file attribute changes, deletions, registry key creation, and more.
Process Monitor is a free tool from Microsoft that displays file system, registry, process, and other activities on the system. It’s an invaluable tool for troubleshooting Windows problems as well as for malware forensics and analysis tasks. The thoroughness of the tool is also weakness, as the amount of data captured by Process Monitor can easily overwhelm the analyst.
Filters for Sifting Through Process Monitor Data
Finding meaningful events in Process Monitor’s voluminous log file is simpler by using the tool’s filtering capabilities, which allow the analyst to conditions for determining whether records should be shown or hidden. You can define the filters by pressing Ctrl+L in Process Monitor or through the Filter > Filter… menu option. As you can see, the tool comes with several pre-defined filter to eliminate a small set of common Windows events:
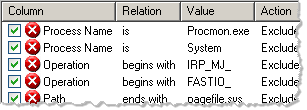
Even with the default filters, there is usually too much noise in Process Monitor’s log file. The good news is that the tool allows the analyst to not only define custom filters—it also includes the ability to save filters as independent entities. This allows the analyst to use custom filters for either hiding “boring” entries or checking the log file for the presence of “interesting” events.
Saving and Organizing Custom Filters
After creating a custom filter with Ctrl+L, you can save it using the Filter > Save Filter… menu option. The tool will remember your filters across sessions; however, it won’t activate it until you load it using the Filter > Load Filter…
To see the filters you defined, select Filter > Organize Filters… This window will allow you to export custom filters to files with the PMF extension, if you want to save the filter for use outside of the local system. The window will also let you load PMF files.
Sample Filters for Malware Analysis and Forensics
Raymond Hodge, whom I met in my reverse-engineering malware course, created several filters for eliminating additional Windows XP noise and for looking for some events associated with malicious software. Raymond allowed me to publish his filters, in the hopes that others can customize them and learn about this aspect of the tool. (Thanks, Raymond, for defining these filters and also for the idea of using them in this manner.)
Raymond’s filters offer a convenient way to examine Process Monitor’s log file for activities that are sometimes associated with malware, such as changing the file’s attribute, deleting a file, creating a registry key, etc.
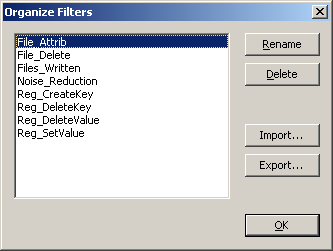
To load these filters, download and extract the archive that contains the filters’ PMF files: process-monitor-filters.zip. Load each PMF file using the Import… button in the window that appears in Process Monitor when you select the Filters > Organize Filters… menu option.
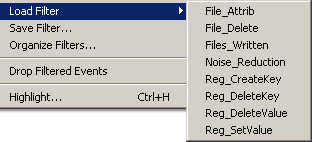
Once the filters are imported, you can load the desired filter by selecting it from the Filter > Load Filter menu:
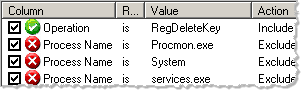
Once the filter has been loaded, you can view and customize its logic by selecting Filter > Filter… or pressing Ctrl+L:
A Warning Regarding Process Monitor Filters
An important caveat when using Process Monitor filters is to be careful not to eliminate meaningful events. For instance, you might create a filter to display only events associated with a particular suspicious process, and as the result not notice malicious activities associated with other processes. Similarly, you might create a filter to conceal activities associated with a common Windows process and not notice malware that runs with the same process name.
Hand-picked related posts:
- 3 Free NirSoft Tools for Malware Analysis
- Using Netsh for Easier Network Setup in a Malware Lab
- Process Hacker as an Alternative to Process Explorer
Just so you know, I teach the malware analysis course at SANS Institute.