Scammers Prescreen Victims for Tech Support Scams via Twitter and Phone
Tech support scammers use Twitter bots to respond to public messages containing words like "virus" and "malware," inviting potential victims to call phone numbers where automated systems profile callers. The prescreening process saves scammers time by filtering for gullible adults who have personal computer problems.
A new twist on the tech support scam prescreens potential victims by contacting them on Twitter and inviting them to call a phone number. This approach appears to be designed to save scammers time by eliminating people who are unlikely to be persuaded by their social engineering tactics.
Using Twitter Bots to Initiate Contact
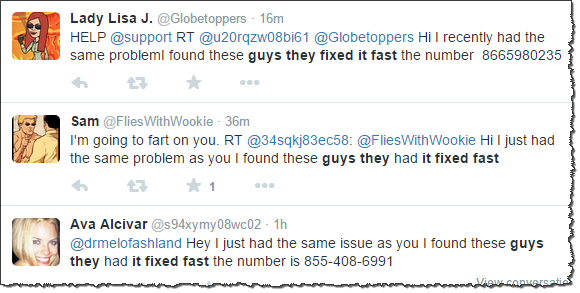
The scam starts on Twitter, where the scammers respond to public messages that include words such as “virus” and “malware”. For example, one user wrote “Show visitors your site is safe from hackers and malware”. The scammer’s bot noticed the message and responded, “Hey I just had the same problem as you I found these guys they fixed it fast the number is 855*408*6991”.

The scammers are hoping to come across individuals complaining about computer security problems, inviting them to call a phone number to reach a service that can help. Sometimes the bots’ messages miss the mark. For instance, one person wrote
“Ebola Virus Must Be Stopped at Source aid organizations need our help”. The scammer chirped, “Hi I recently had the same issue as you I called these guys they had it fixed quick the number is 844*853*2662”.
Profiling Potential Victims by Phone
I used a burner phone to call one of the numbers advertised by the scammers. I was greeted with a recording of a male voice, speaking in perfect American English:
“Please listen carefully so we can route your call properly. If you’re experiencing issues with your desktop computer, or think you may have a virus, or if you have a computer security issue, please press 1. If you’re experiencing issues with you iPhone, iPad, Android or Xbox device, please press 2.”
If the caller indicates that the call is regarding a problem with a mobile or gaming device, the recording states, “Unfortunately, we cannot support or service smartphones, Android or Microsoft devices. Please contact your manufacturer directly. Good bye.” If the caller states that the issue is with a business computer, the recording responds, “Unfortunately we’re unable to support business computers at this time. Please contact your manufacturer directly.”
You can hear the recording below or download the MP3 file
I’ve captured.
Selecting the menu option related to a personal computer leads to the prompt, “If you are 21 or older, please press 1. If under 21, please press 2.” If the caller presses 2 at that point, he or she hears, “You must be 21 years of age or older for us to assist you. Good bye.”
If the potential victim indicates that he or she is 21 or older and is calling regarding a personal computer, then the recording states in a female, computer-generated voice, “Thanks, good bye” and hangs up. (How rude.)
Allowing Victims to Self-Select
Why hang up on the caller? And who would call the phone number in response to an unsolicited Twitter message in the first place? What game are the scammers playing?
I have a theory. I wrote earlier about social engineering tactics that involve allowing victims self-selecting themselves. The goal of such tactics could be to save scammers from wasting time on interactions with people who are unlikely to be persuaded.
In the case of the scam outlined in this post, victims are screened to be not only gullible, but also to have a problem with a personal computer that they need to resolve. Also, they are over 21, which indicates that they are adults with ability to make contract and spending decisions.
The automated phone system hung up on the caller probably because it received all the details it needed to refer the potential victim to a human scammer, presumably after noting the person’s caller ID. It’s possible that the scammer will eventually call the person’s phone number. At that point, the phone call will not be completely unexpected, and the scammer will know that they’re dealing with the kind of person who will likely be susceptible to their tactics.
When investigating this campaign, I observed multiple Twitter bots responding to Twitter users with invitations to call several phone numbers, all of which seem to lead to the same automated system. (See screenshot below.) The objective of such interactions is to save scammers time and, therefore, money, by using automation to profile victims and helping avoid dealing with people who are not worth the scammers’ time. It’s an interesting twist on the classic tech support scam.