Analyzing Suspicious PDF Files With Peepdf
Peepdf is a Python-based tool for analyzing malicious PDFs with an interactive shell for navigating file structures. It highlights suspicious objects like AcroForm, OpenAction, and JavaScript, automatically decodes streams, and provides commands for analyzing encoded JavaScript and emulating shellcode.
Attackers continue to use malicious PDF files as part of targeted attacks and mass-scale client-side exploitation. Peepdf, a new tool from Jose Miguel Esparza, is an excellent addition to the PDF analysis toolkit for examining and decoding suspicious PDFs.
For this introductory walk-through, I will take a quick look at the malicious PDF file that I obtained from Contagio Malware Dump. If you’d like to experiment with this file in an isolated laboratory environment, you’re welcome to download the malicious PDF from my server; the password to the zip file is the word “infected”.
Peepdf is written in Python. It doesn’t have a graphical user interface; however, people used to command-line interfaces will feel very comfortable using the tool. This applies especially to its interactive mode, which drops you into the tool’s shell that allows you to navigate through the PDF file’s structure and explore its contents.
Examining a PDF File for Suspicious Characteristics
After installing Peepdf (instructions below), you can simply scan the PDF file by using the “peepdf file.pdf” command to obtain information about the file. When you’re in the tool’s interactive shell, you can view these details using the “info” command.
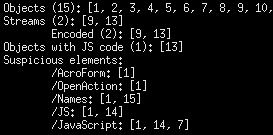
When asked to show you “info”, Peepdf will point out suspicious objects that are often used for attacks. In the example below, the tool highlighted AcroForm, OpenAction, Names, JS and JavaScript because these PDF elements are often misused. It also pointed out that object 13 seems to contain JavaScript, which is a common component of PDF exploits.
Examining Suspicious Object Contents in the PDF File
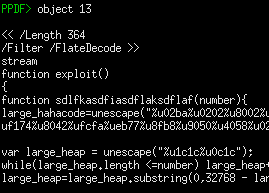
Use the “-i” parameter to Peepdf to enter its interactive mode (“peepdf -i file.pdf”). Once in the interactive shell, you can use the “object” command to examine contents of the desired object. For instance, we saw earlier that object 13 contains JavaScript. Typing “object 13” will show the object’s contents, including the embedded JavaScript. Peepdf will automatically decode the contents of the stream that includes JavaScript using the appropriate filters.
In our example, the variable “large_hahacode” seems to include shellcode that the analyst would want to extract and examine to understand its capabilities.
Peepdf includes additional commands to help you analyze contents of encoded JavaScript variables and execute JavaScript commands. This might help with deobfuscation, though I haven’t experimented with Peepdf enough yet to explore these capabilities of the tool. Peepdf does provide a convenient way of calling the “sctest” command from its interactive shell; this can help you emulate the execution of shellcode.
To learn more about Peepdf’s capabilities to analyze contents of malicious PDF files, see the tool’s webpage for usage highlights and its documentation for a full listing of its commands.
Installing Peepdf on Linux
I use REMnux for malware analysis tasks that can be performed on Unix, and hope to include Peepdf in the next release of this distro. Installing Peepdf on REMnux was straightforward, and I doubt you’ll run into challenges on other Linux platforms. Once logged into REMnux, assuming that the host is connected to the Internet, type:
sudo apt-get install python-pyrex
svn checkout http://python-spidermonkey.googlecode.com/svn/trunk/ python-spidermonkey
cd python-spidermonkey
python setup.py build
sudo python setup.py install
sudo ldconfig
cd .. && rm -rf python-spidermonkey
mkdir peepdf && cd peepdf
wget http://peepdf.googlecode.com/files/peepdf-0.1.zip
unzip peepdf-0.1.zip && rm peepdf-0.1.zip
ln -s /usr/local/bin/sctest .
If you like analyzing malicious programs, take a look at the Reverse-Engineering Malware course
I teach at SANS. If you’re just getting to know malware, you might also like my Combating Malware course.
Related: