NoScript is one of the most popular add-ons for Firefox. It’s designed to disable scripting and other mobile code to secure the browser. Yet, using Firefox with NoScript is like driving on a city street with Stop signs on every block: You have to enable scripting for every website you visit and didn’t have a chance to whitelist.
Security-conscious people are OK with the interruptions and are willing to invest time into building up a whitelist of commonly-visited sites. Yet, I suspect many NoScript users automatically click “allow” to enable scripting on the site without much thinking. And I bet many people uninstall the add-on altogether to avoid making scripting decisions.
If NoScript’s script whitelisting feature isn’t for you, you can still benefit from other ways in which it strengthens security of Firefox: namely, Application Boundaries Enforcer (ABE) and Cross-site scripting (XSS). Simply enable scripts globally using NoScript’s options menu:
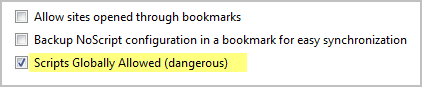
XSS and ABE-related features of NoScript will remain enabled, and I recommend keeping them that way:
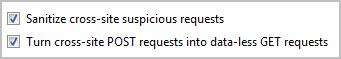
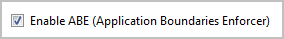
If you’re using Firefox and gave up on NoScript, give it a try after allowing scripts to run by default. Though you’ll lose the ability to selectively enable mobile code on trusted websites, you’ll retain some of the add-on’s benefits for strengthening security of the browser.
— Lenny Zeltser