NetworkMiner for Analyzing Network Streams and Pcap Files
NetworkMiner is a free Windows tool for network forensics that displays hosts, HTTP parameters, clear-text content, and credentials from live or captured traffic. It automatically carves files from network streams—especially useful for extracting potentially malicious files for further analysis.
NetworkMiner is a free Windows utility for analyzing network traffic. It can examine live traffic that the system is sniffing off the wire. It can also explore contents of previously-captured traffic saved in the pcap format. The tool is designed to only display the details most relevant to network forensics. It is especially useful for carving packet captures to extract the files they contain, so you can further analyze the files that might be malicious.
One Use-Case for NetworkMiner
Consider a scenario where you’re analyzing a suspicious website, wishing to understand the way that it might try attacking its visitors. One way to approach this challenge is to browse the website using a Windows laboratory system designated for this type of work. In this case, your hope might be to have the system attacked and infected, so you can understand the nature of the threat.
There are several tools that could capture relevant details about the attack, so you can analyze them to understand what transpired. For instance, CaptureBAT can capture not only process-level activity on the laboratory system, but also create a pcap file of the observed network traffic. You can also run a dedicated network sniffer, such as tcpdump or Wireshark’s dumpcap, or use the sniffer built into NetworkMiner.
NetworkMiner in Action
For a quick demonstration of NetworkMiner, I’ll use the pcap file I created for the network forensics puzzle called Ms. Moneymany’s Mysterious Malware. (Though that context is over, you may want to download its files and experiment with them if you haven’t done so already.)
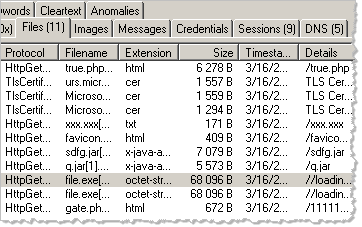
After you load the pcap file into NetworkMiner, it parses the file and presents several tabs with various aspects of the traffic and its contents. These include:
- The observed hosts, including their DNS names, IP addresses and ports used during the monitored period
- HTTP parameters sent to web servers as part of the observed session
- Clear-text ASCII contents extracted from the network streams, including a separate tab for any captured credentials
- The files exchanged between the hosts during the monitored period
NetworkMiner automatically carves out the files found in the network stream, saving them to a local folder. One of the reasons for using an dedicated laboratory system when using the tool in this capacity is that the files might be malicious, and you may get infected if you don’t handle them carefully.
To view the extracted file, right-click on the file of interest in NetworkMiner’s Files tab, then select open folder.
To experiment with the pcap file I mentioned in this write-up, read and consider solving the Ms. Moneymany’s Mysterious Malware network forensics puzzle. Also check out my follow-up malware analysis challenge. For more ways of using NetworkMiner, look over to the NETRESEC Network Security Blog.
Update: Though NetworkMiner is designed to work on Windows, you can get it to run on Linux, including BackTrack.