
Network honeypots offer defenders an enticing opportunity to learn about attackers' presence and methods by incorporating deception into the organization's security program. The open-source tool Modern Honey Network (MHN) by Anomali drastically simplifies the tasks of installing and managing low-interaction honeypots. Armed with MHN and access to a public cloud provider, anyone can start experimenting with honeypots.
A key component of the Modern Honey Network is an easy-to-use web application called MHN Server. I'll explain how you can install it. First, let me show you why setting it up might be worth your while.
MHN Server allows you to easily deploy honeypots to other systems. To do this, you'll select "Deploy" in your MHN Server web app to generate a script for automatically deploying the desired honeypot to a system of your choice. The script will automatically configure the honeypot to centrally report to your MHN Server for centralized management and oversight.
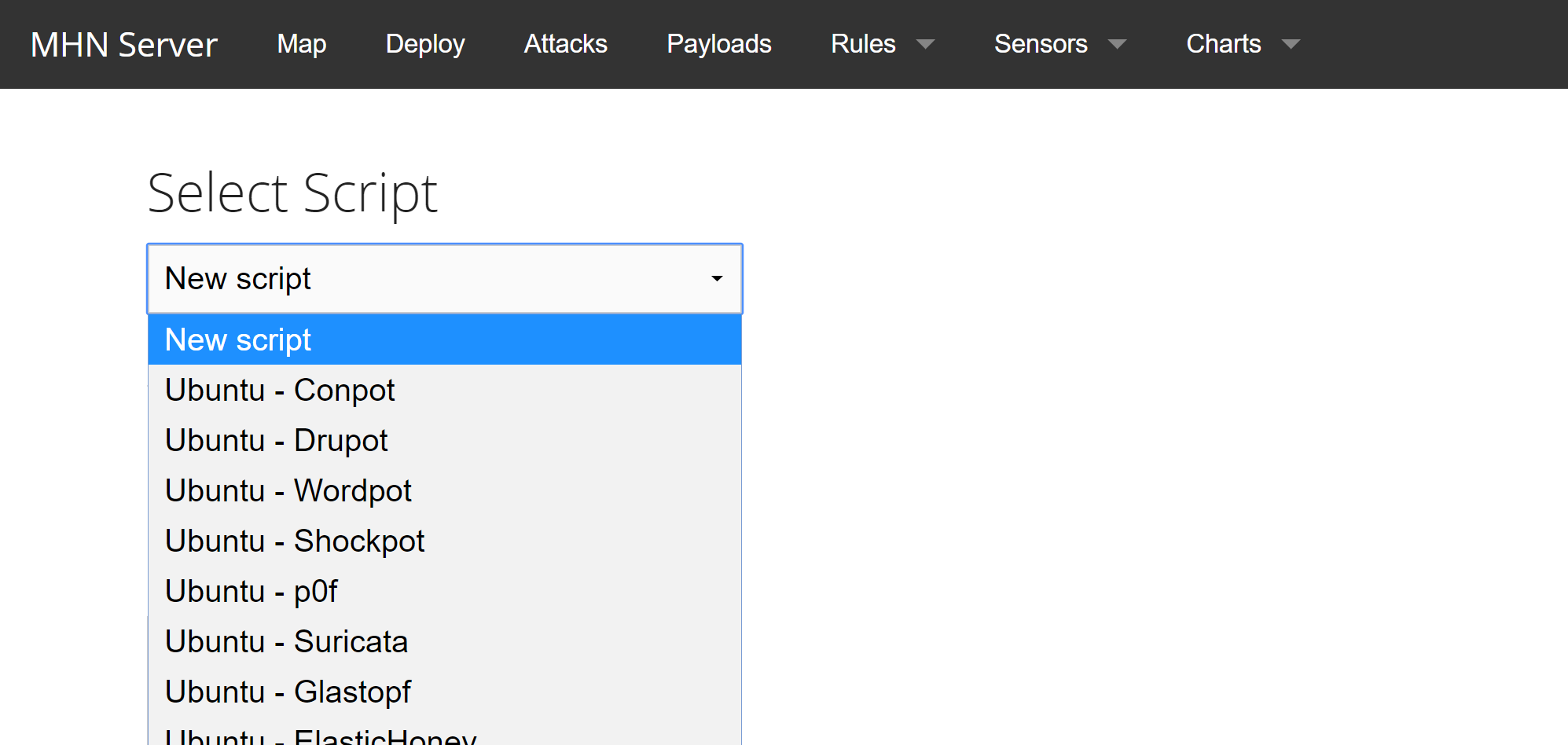
The list of Honeypots that MHN Server supports includes Conpot, Cowrie, Dionaea Glastof, Wordpot, Shockpot, and others. It also supports intrusion sensors, such as Snort.
Installing MHN Server
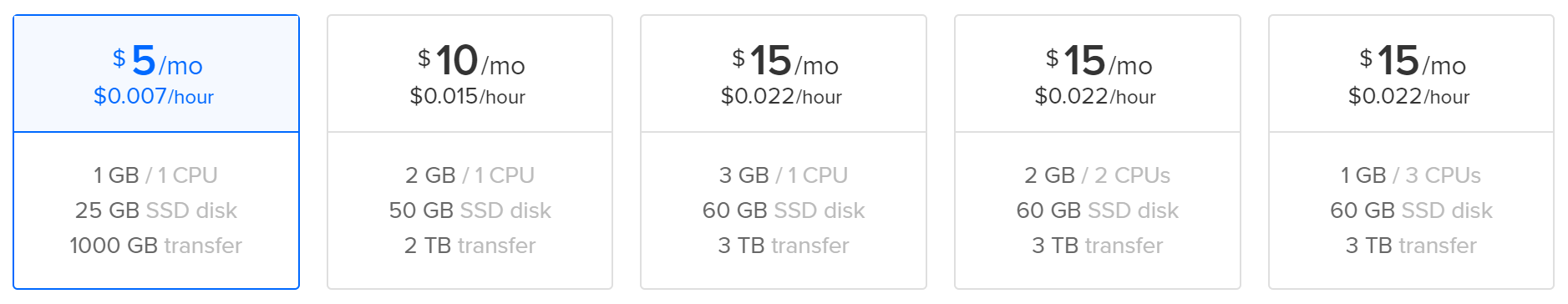
A convenient way of starting to experiment with honeypots and the Modern Honey Network is to deploy an inexpensive Linux systems at public cloud provider such as DigitalOcean (the link includes my referral code). I like this provider in part because it offers a low-end virtual private server instance for as little as $5 per month. You can deploy a "droplet" running Ubuntu there in a few clicks.
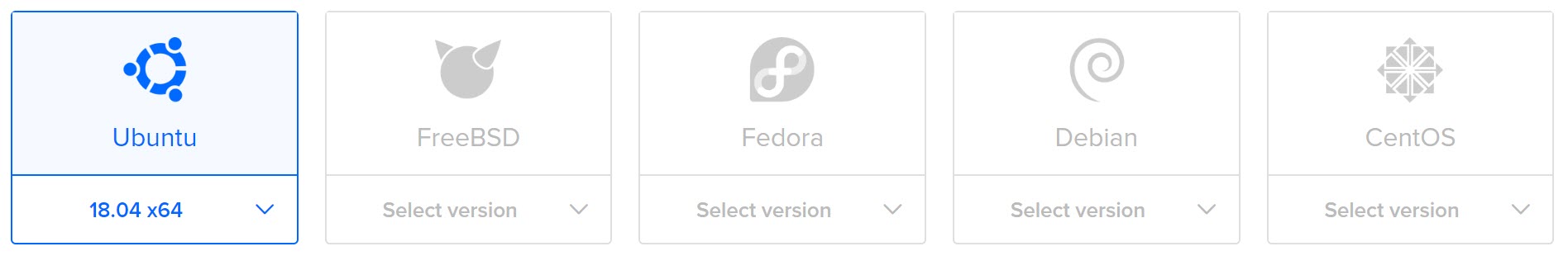
For the purpose of this example, I selected Ubuntu 18.04, then the $5/month VM configuration:
Boot up your new system, log in, then run the following commands as root:
apt-get -y update apt-get -y upgrade apt-get -y install git cd /opt/ git clone https://github.com/threatstream/mhn.git cd mhn ./install.sh
The script will automatically installing the needed software. Be patient, this can take a while. It will eventually prompt you for a few configuration parameters. These will include the email address of the MHN Server administrator--the script calls this "Superuser email"--this will be your username. The script will also prompt you for the "Superuser password."
Once the installation finishes, you can connect to your MHN Server by directing your browser to the server's IP address or hostname over HTTP. (If want to use HTTPS, you'll need to take a few configuration steps.)
If you don't want to send anonymized data about your MHN deployment to Anomali, run the following command on the MHN Server:
/opt/mhn/scripts/disable_collector.sh
Harden the configuration of your server, which might involve restricting remote SSH access and configuring its firewall.
Deploying an MHN Honeypot
After logging into your MHN Server app, select "Deploy" from the top menu. Then under the "Select Script" dropdown, select the desired honeypot or sensor. For example, to deploy a Dionaea honeypot, I selected "Ubuntu 14.04/Centos 7 - Dionaea." The app generated the following one-line script to deploy this honeypot:
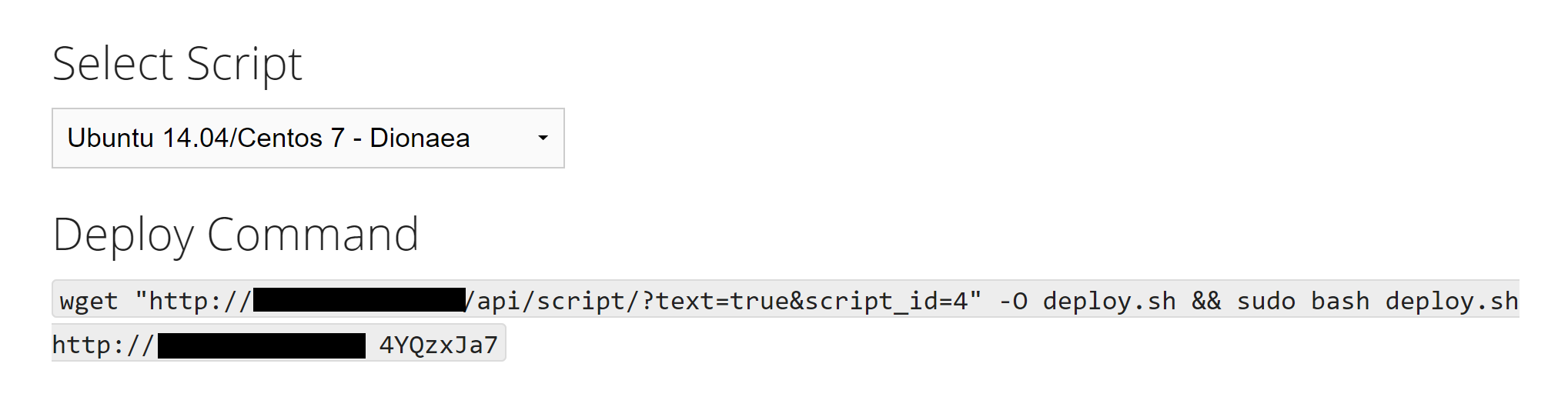
After creating a Centos 7 VM in the public cloud, I logged into it, entered the command "yum install wget", and pasted the Dionaea deployment command . I used Centos 7 for Dionaea because I couldn't easily get an Ubuntu 14.04 VM, and the script failed on a newer version of Ubuntu. I was able to deploy "Ubuntu - Wordpot" on an Ubuntu 18.04 VM.
Centrally Monitoring Your MHN Honeypots
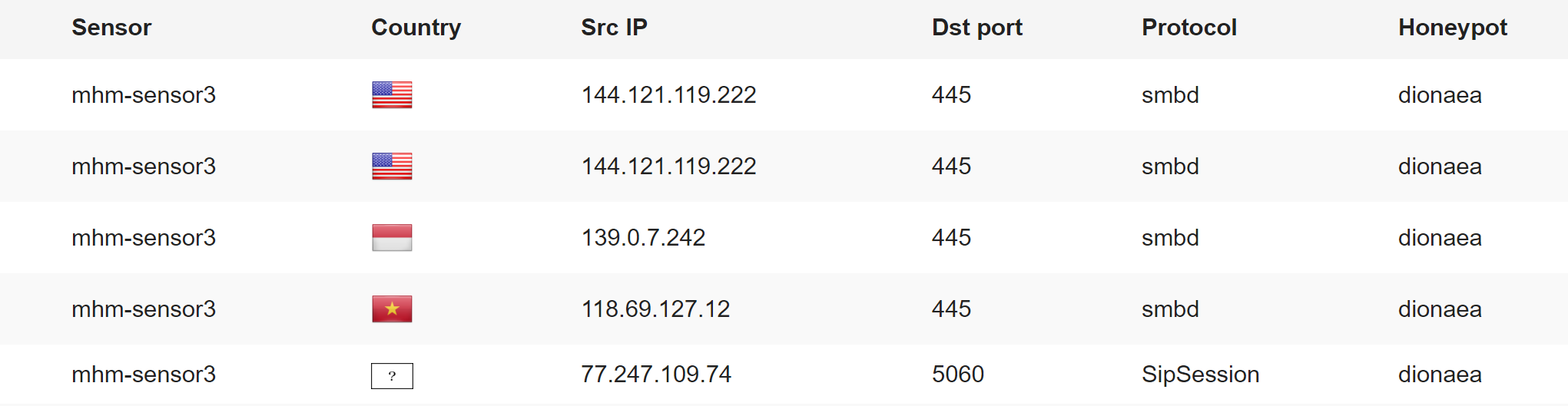
MHN Server lets you centrally observe the data captured by your honeypots. For instance, it displayed the following attack summary minutes after I deployed my first honeypot:
Start Experimenting, See What You Learn
As you can see, the Modern Honeypot Network tool makes it convenient to deploy and oversee a variety of honeypot sensors with minimal expense. If you'd like to start experimenting, spin up a few low-end VMs using your favorite public cloud provider, install MHN Server software on one of them, and deploy a few honeypots to others. The data you'll gather will help you understand attack methods and might inspire you to experiment and learn in other creative ways.