Market Segmentation in Computer Attacks
Computer attackers segment victims by organization size (focused enterprise targets vs. mass-scale SMBs), geography (paying more for North American infections), and industry. Defenders need to understand this segmentation to align defenses with actual threats rather than treating all risks equally.
In business, the the term market segmentation emphasizes the importance of viewing one’s customers as belonging to different groups. The grouping can be based on the organization’s size, budget, location or other factors that result in one market segment being meaningfully different from the other. Computer attackers are paying attention to this concept; defenders should understand the notion of market segmentation in the context of information security.
Market Segmentation by Legitimate Businesses
Market segmentation is regularly used by legitimate businesses. For instance, airlines price tickets differently for leisure and business travelers, due to the differences in these customers’ priorities and willingness to pay. Similarly, Starbucks sells a number of beverages to suit the preferences across the spectrum of its clientele, even including tea on its menu to cater to customers who don’t want coffee. By understanding the differences between the segments, the company can develop slightly different products or services for each type of customer, and may be able to price its products in a way that extracts the most surplus from the market.
Market Segmentation by Computer Attackers
Market segmentation also increasingly employed by computer attackers. They do this in several ways, the most common approach involving grouping potential victims by organization size. I wrote about this trend in an earlier post Evolving Threats: The Long Tail of Potential Data Breach Victims, where I outlined two distinct market segments:
- Focused Targets: A portion of the total population of potential victims—perhaps 20%—are large enterprises that can serve as high-value, focused targets. These are targeted attacks, a portion of which fall into the category of Advanced Persistent Threat (APT), though some of these might still be attacks of opportunity.
- Mass-Scale Targets: Some attackers pursue a larger number of smaller companies and individuals. Executing and deriving “value” from such attacks involves a high degree of automation for infection campaigns and data processing.
Other ways in which computer attackers segment the “market” is by the geographic location of victims. For instance, malware distribution (e.g., pay-per-install) services pay the affiliates more for infecting a system in North American than the one in Asia. Industry (e.g., the type of data processed) is yet another way that attackers can perform market segmentation.
Data from the Verizon Data Breach Investigations Report
Among the many observations in the the 2011 Verizon Data Breach Investigations Report, was the increased number of breaches that occurred in small businesses. Since those days, more and more small and mid-sized businesses have been falling victims to such incidents.
“Typically, such organizations represent smaller, softer, and less reactive targets than, for instance, financial institutions. Criminals may be making a classic risk vs. reward decision and opting to ‘play it safe’ in light of recent arrests and prosecutions following large-scale intrusions into Financial Services firms. Numerous smaller strikes on hotels, restaurants, and retailers represent a lower-risk alternative, and cybercriminals may be taking greater advantage of that option.”
Commenting upon this trend, Rich Mogull pointed out, “Using automated systems against weak targets and riding the associated economies of scale can be very lucrative, and it’s not surprising to see these targets multiply.”
The Internet Threat Hierarchy
Dan Guido discussed the different types of computer attacks in a talk that discussed The Exploit Intelligence Project. I especially liked his illustration of the threat hierarchy:
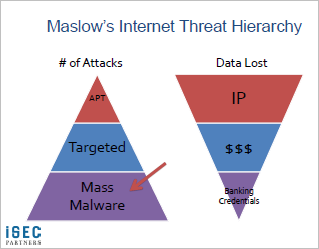
Even in the layers of the pyramid occupied by “APT” and “Targeted,” we can be more specific. Scott J. Roberts called for more exact taxonomy of such attacks, which effectively would help us better understand market segmentation from attackers’ perspective. Scott propose the following terms:
- “State Sponsored Espionage (What we now call APT)
- Financially Motivated Criminals
- Nationalist Activists
- Criminal Activists (So called Hactivists)“
Implications for Computer and Data Defenders
Information security professionals need to better understand the way computer attackers view market segmentation. This will help us understand the differences in threats across various industries, organization sizes and other potential victim groupings. In turn, having this view will lead to defenses being more in line with the actual threats and, perhaps, to security products that are better aligned with the corresponding market segments.