Analyze Memory of an Infected System With Mandiant's Redline
Mandiant's free Redline tool triages potentially compromised hosts through live memory analysis, replacing Audit Viewer. It uses Memoryze to capture memory, assigns Malware Risk Index scores using built-in heuristics, and can locate memory sections injected into processes.
Mandiant’s free Redline tool is designed for “triaging hosts suspected of being compromised or infected while supporting in-depth live memory analysis.” The new utility is meant to replace Audit Viewer, which was Mandiant’s earlier memory analysis tool. Both programs rely on Memoryze for capturing the memory image of the live Windows host, though they can also examine “dead” memory image files.
Redline’s present version mostly mimics the functionality of Audit Viewer—albeit in a more streamlined interface. However, Mandiant plans to expand Redline “to include significant new capabilities unavailable in Audit Viewer,” according to the FAQ.
After launching Redline, the user is presented with several options, which include using an existing memory image file and examining the local computer:
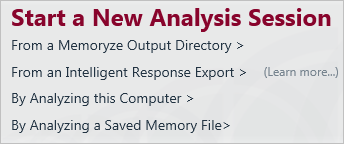
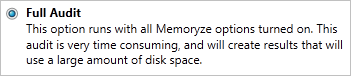
When scanning a local system, the user can select what type of data Redline will extract from memory. The options are Quick Scan, Standard Scan, Full Audit and Custom. I recommend using Full Audit despite it being slow, in part because it includes the extraction of strings:
Once the scan completes, the user is presented with an interactive interface for examining the findings. One of the tool’s useful features is its ability to automatically assign a “Malware Risk Index” (MRI) to memory artifacts based on several built-in heuristics. Redline flips the rating in comparison to Audit Viewer, 100 as the riskiest value and 0 as the least risky one. (For more on MRI, see the Redline FAQ.)
Another feature of the tool allows it to locate and examine memory sections that may have been injected into processes:

Redline includes numerous other features that should prove useful to computer forensic analysts and incident responders. I’m looking forward to seeing this tool evolve.