There have been several attempts to standardize the conventions used to name malware samples. Yet, picking malware names in a consistent manner is harder than one might assume. Security companies tend to assign names to malware according to variations of the CARO naming scheme. CME was another effort for assigning identifiers to malicious programs; this project focused on high-profile malware and is no longer active.
The CARO Naming Scheme
The security community benefits when security companies agree on a name when referring to a particular malware specimen, For instance, a single name can act as a tag to the relevant information resources as tools, so that individuals can quickly locate them when responding to malware infections. While agreeing on a single name for a particular sample is hard to accomplish in most cases, companies can agree on the general approach to assigning names to malware specimens.
A naming scheme that came the closest to being adopted by antivirus firms is CARO. According to Dr. Vesselin Bontchev,
"The fundamental principle behind the CARO Malware Naming Scheme is that malware should be grouped into families, according to its code similarity. The other fundamental principle is that malware names should be unique - that is, every different malware variant, no matter how minor, should have a different name from that of any other malware."
The resulting format follows the pattern “[<type>://][<platform>/]<family>[.<group>][.<length>].<variant>[<modifiers>][!<comment>]”, where the tags in square brackets are optional.
Though CARO wasn’t universally adopted directly, security companies base their naming conventions on CARO for the most part. For instance, Microsoft Malware Protection Center names malware like this:
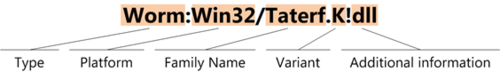
(The diagram above was created by Microsoft.)
The Common Malware Enumeration (CME) Initiative
Even when companies use a CARO-based naming scheme, the firms might differ in how they name identical malware specimens, for instance by using different approaches to selecting the Family Name component. To aid companies in referring to a popular malware specimen by a common name, MITRE launched the Common Malware Enumeration (CME) initiative.
According to the FAQ, the goals of CME were to:
"Reduce the public’s confusion in referencing threats during malware incidents.
Enhance communication between anti-virus vendors.
Improve communication and information sharing between anti-virus vendors and the rest of the information security community.”
The CME effort is no longer active. According to the CME website, CME identifiers were meant to be assigned to “high-profile threats.” However,
"The changed nature of the malware threat since late 2006—away from pandemic, widespread threats to more localized, targeted threats—greatly reduced the need for common malware identifiers to mitigate user confusion in the general public."
It’s unfortunate that CME is no longer being maintained, but I understand the realities that make efforts such as CME impractical. Yet, there is still plenty of popular malware that affects a lot of people, and we could benefit from assigning common names to malicious programs that catch the public’s eye. Instead, security companies tend to assign various eye-catching names to popular specimens, as I’ve discussed in a follow-up post.