Internet advertisement networks provide attackers with an effective venue for targeting numerous computers through malicious banner ads. Such malvertisements may take the form of Flash programs that look like regular ads, but contain code that attacks the visitor’s system directly or redirects the browser to a malicious website. Malicious ads can also be implemented without Flash by simply redirecting the destination of the ad after the launch of the campaign.
How are such campaigns conducted? What, if anything, can we do about them? We can begin making sense of malicious ad practices by examining some examples of high-profile malvertising incidents.
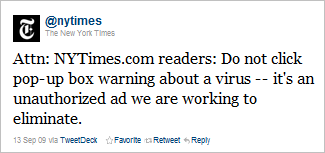
Rik Ferguson from Trend Micro described an incident when the New York Times was hosting a banner ad that attempted to social-engineer people into installing a rogue antivirus tool. According to Rik, “the problem may have been ongoing for upwards of 24 hours” before the New York Times noticed the malicious nature of the ad and disabled it.
In another example, the London Stock Exchange website was also observed inadvertently serving malicious ads to its users, as described by Paul Mutton. This incident was traced to a possible breach at Unanimis—the company serving the ads the London Stock Exchange and many other companies.
Elad Sharf from Websense analyzed the Unanimis malvertising incident that affected a number of high profile web properties. He noted that such malvertising campaigns are attractive to attackers because they “can be easily spread across a large number of legitimate Websites without directly compromising those Websites.”
Mary Landesman from ScanSafe/Cisco pointed out that the list of popular websites serving malicious ads in the recent years included Hoovers.com, USNews.com, Tucows.com, TheOnion.com, SpeedTest.net and many others. She also explained that malvertisements aren’t limited to a particular ad network; they’ve been “delivered via DoubleClick (Google), YieldManager (Yahoo!), and rad.msn.com (Microsoft),” and also through webmail services, such as Windows Live (Hotmail) and Yahoo! Mail.
Jiri Sejtko from Avast! also reported that large scale ad-networks are often responsible for delivering malvertisements. For one malvertising campaign tracked by Avast!, the most compromised services were YieldManager.com (Yahoo!) and Fimserve.com (FOX Audience Network), which delivered more than half of the malicious ads in that incident.
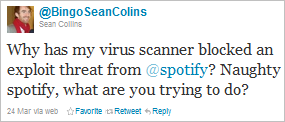
While most of the malvertising campaigns have affected users of web browsers, an incident involving Spotify showed that applications can be used as a similar attack vector. Patrik Runald at Websense described how Spotify, a music streaming service, was displaying a malicious ad to the users of its media-playing application. The app rendered the ad and its malicious code as if it were a browser without requiring user interaction. “If you had Spotify open but running in the background, listening to your favorite tunes, you could still get infected.”
The wide reach that attackers can have by delivering client-side attacks through advertisement networks—and the difficulty with which we’ve hard curtailing malvertising practices—suggests that this attack vector isn’t likely to disappear soon. We need to find a better way of dealing with it.
This is the first post a series of malvertising-related posts. You can also learn:
- The Mechanics of Malicious Ads
- How Malicious Ad Campaigns Are Protected
- How Malicious Ads Are Deployed
- Dealing With Malicious Ads - Who and How?