One way to characterize computer attackers is to consider whether they focus on specific high-value targets or whether their efforts span a large number of low-value targets en masse. The "long tail" of numerous potential victims may be very attractive to some computer attackers, but requires the scale of operations and expertise different from those that support enterprise-focused intrusions.
What Is The Long Tail?
The notion of the long tail refers to the distribution of occurrences that gradually "tails off" asymptotically. A key property of this distribution is that the least-frequent occurrences comprise roughly 80% of the total population; these vast occurrences are the long tail.
The the case of data breaches, the long tail of potential victims is comprised of numerous small and mid-sized businesses (SMBs).
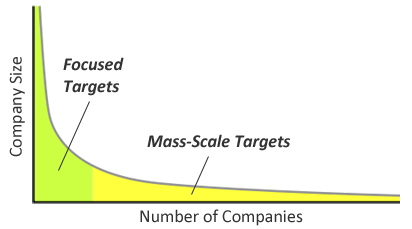
Focused Targets
From the attackers' perspective, approximately 20% of the total population of potential victims are large enterprises that can serve as high-value, focused targets.
Attackers pursuing focused targets are more likely to use zero-day exploits or custom malware to compromise victims' defenses, spread internally, exfiltrate the data and maintain continued presence. Attacks on focused targets might take the form of industrial espionage.
Mass-Scale Targets
Some attackers prefer quantity over quality, pursuing a large number of smaller companies and individuals that comprise around 80% of the total population of potential victims—the long tail. Each of these entities might not possess as much as the larger enterprises. However, they are attractive targets because they tend to have weaker defenses and because there are lots of them.
Attackers pursuing mass-scale targets might send out spam to reach numerous potential victims. They might distribute malicious banner ads to infect many desktops in drive-by attacks using exploit kits. They might use commercial-grade malware platforms such as Zeus to steal funds from SMBs.
The Attractiveness of the Long Tail
I expect attackers to continue specializing in their pursuit of victims, some developing expertise in compromising focused targets, while others becoming really good at capturing mass-scale targets. This makes sense from a "business" perspective of the attackers.
I wonder how quickly the attackers will see the "market" of large, focused targets as saturated. Legitimate IT vendors that have captured much of the large enterprise market are looking towards SMBs for growth. Similarly, I expect attackers to see the long tail of mass-scale targets as an attractive "business" opportunity that has much room for growth. In many ways, this future is already here.
To paraphrase Chris Anderson writing about the long tail, combine enough small targets and you've got a market bigger than the enterprises.
In a follow-up post, I explore how security product and service companies look at the long tail of potential customers.