Exploring LinkedIn Look-Alike Email Spam Campaigns
LinkedIn-themed spam effectively distributes malicious links because users are conditioned to receive and click LinkedIn emails—often without visiting the site directly. Campaigns have led to exploit kits, rogue pharma sites, and affiliate fraud. Legitimate LinkedIn emails never include attachments.
In an earlier note I discussed why malicious LinkedIn activities seem less prevalent
Facebook and Twitter ones. Yet, the users of LinkedIn aren’t immune to risks. The most prevalent form of scams and fraud associated with LinkedIn appears to be spam that mimics the look of LinkedIn emails. This isn’t surprising, considering that the service heavily relies on email to communicate with its user base—sending weekly social network updates, invitations to connect, group announcements, and so forth.
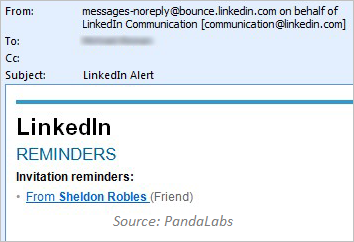
Spam messages that look like they come from LinkedIn tend to include links to malicious websites. For instance, PandaLabs described a spam campaign that included a fake LinkedIn invitation to connect and included a link to a rogue pharma website:
Another spoofed email mimicked LinkedIn’s “So now you’re on LinkedIn: What’s next?” message, but pointed to a non-reputable site—one sample I saw used vqqjsmbl.info and another ylbochqs.info:
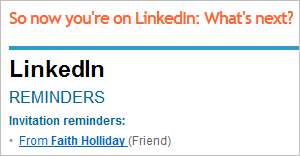
Kimberly at StopMalvertising described an incident where an email message bearing the same subject directed the victim to a website hosting an exploit kit that attempted to infect the person’s PC with ZeuS.
In another example, described by the Spam Daily blog, the spoofed email message appeared to be a note from someone the recipient just met. The sender provided an affiliate program link that credited the attacker for referring people to legitimate websites, such as a loan application service:
“It was great talking to you the other day. Good luck on all your projects….I’m sure they’ll turn out great. BTW…here’s the site I told you about that set me up with all the financial aid for my online masters.
http :// gy-qes. daukskosos. com/ 687cf7eeef7988de3401117b6eacfbcb4d9298”
Yet another example of LinkedIn-themed spam used the subject “LinkedIn account has been blocked” and included a malicious link:
“Your LinkedIn account was blocked due to inactivity.
To remove the restrictions please [click here]{}
Thank you for using LinkedIn!”
These email messages appear to be effective. One email recipient expressed her confusion on the LinkedIn Q&A site:
“I don’t know if this a hoax or authentic. If it is real, can you please tell me why my account has been blocked.”
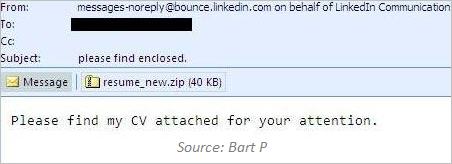
LinkedIn can also be used as a pretext for including malicious files as email attachments. This is rarely uncommon, because legitimate LinkedIn emails don’t include attachments. In one case, Bart P described a spoofed LinkedIn email that claimed to include a CV, but was actually a trojan executable:
Users of LinkedIn are conditioned to receive LinkedIn emails and click on the embedded links. After all, they tend to visit linkedin.com less often than facebook.com, commonly relying on email messages to keep up with their LinkedIn network. As the result, LinkedIn-themed messages provide an effective pretext for distributing malicious links.
Examples above show that such links have taken email recipients to websites hosting exploit kits, affiliate link trackers, and rogue pharma sites. I’m surprised that I haven’t encountered examples where LinkedIn look-alike spam phished users’ logon credentials. Have you?
This post is part of a series that explores LinkedIn scams, fraud and information security risks. The other posts are: