Time to Let Go of Java in the Web Browser: How to Disable It
Java exploits have become the top moneymaker for exploit kit authors, yet few people regularly use Java in browsers. The likelihood of being targeted overpowers the benefits. Disable Java in browsers or use NoScript to allowlist sites; keep JRE patched with Secunia PSI if you can't remove it.
I agree with Brian Krebs: Having Java Runtime Environment (JRE) as part of your web browser has become a major liability. As he put it, “attacks against Java vulnerabilities have fast emerged as the top moneymaker for authors of the best-selling ‘exploit kits,’ commercial crimeware designed to be stitched into hacked or malicious sites and exploit a variety of Web-browser vulnerabilities.”
I often see Java targeted by exploit kits; yet, not many individuals actually use Java in their browser on regular basis. We’re at a point when the the likelihood of it being targeted by a malicious website overpowers the benefits that most people derive from having JRE installed.
To quickly check whether Java support is enabled in your browser, visit Oracle’s How do I test whether Java is working on my computer? page. If you see the message “Your Java is working,” then Java is installed. The lack of this message implies that Java cannot be automatically invoked through the browser, which—in the context of this note—is a good thing.
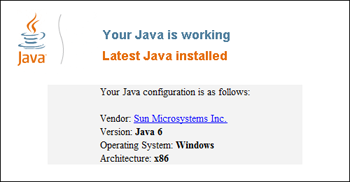
Truth be told, some useful applications are still written in Java and expect to be invoked through the browser. If you cannot simply uninstall Java from your system, you have a few options to limit your exposure to Java exploits:
- If using Firefox, use the NoScript extension to only allow Java on allowlisted sites.
- If using Google Chrome, launch the browser with the “-disable-java” parameter unless you need Java support.
- If using a 64-bit Windows platform, install the version of Java that doesn’t match the version of the browser you typically use. For instance, if you normally use 64-bit Internet Explorer, only install the 32-bit version of Java.
- If using Internet Explorer, you can disable Java through the “Tools > Manage Add-ons > Show: All add-ons” menu; you’ll need to restart. However, I haven’t found a way to re-enable it without reinstalling Java; for some reason, the Java add-on doesn’t show up in the list after you disable it.
- If using Firefox, disable Java through the “Tools > Add-ons > Plugins” menu, and enable it when you need it. You won’t even to restart the browser.
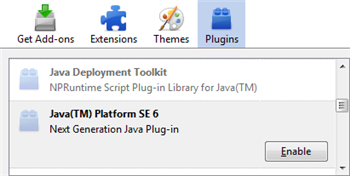
If you cannot uninstall or disable Java access through your browser, be sure to keep your JRE up to date with the latest security patches. The best way to accomplish this is on a single end-user’s system probably with Secunia Personal Software Inspector (PSI).
Do you have other tips for controlling access to Java through the web browser?