Cheat Sheet for Creating Security Assessment Reports
There's surprisingly little online guidance about creating good security assessment reports. This one-page cheat sheet covers the general approach, data analysis, methodology documentation, scope definition, conclusions, and report qualities—available in HTML, PDF, and Word formats.
There is surprisingly little information online about creating good information security reports. You’ll easily find tips on performing web applications assessments, policy reviews and penetration tests, but it’s harder to locate advice regarding the best way to analyze the data and communicate the assessment’s findings.
To ameliorate this situation, I created a 1-page cheat sheet with tips for creating an information security assessment report. It includes some of the the assessment advice I’ve shared on this blog as well as additional tips, covering the following areas:
- General Approach to Creating the Report
- Analysis of the Security Assessment Data
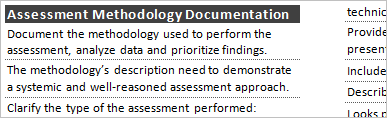
- Assessment Methodology Documentation
- Scope of the Security Assessment
- Documenting Conclusions
- Qualities of a Good Assessment Report
It’s available in HTML, PDF and Word formats, so you can print or customize the cheat sheet for your own needs. Thanks to Dave Shackleford and John Strand for their feedback on the draft of this cheat sheet.
The only thing I like better than reading cheat sheets is creating them. That’s why you’ll see a bunch of them on my website. I hope you find the new addition, which focuses on security assessment reports, useful.