Which of the many information security controls that an organization could implement should it focus on implementing? I don’t think one can answer this question in a generic sense, especially since there is little data to indicate what actually, really works in security. However, I can recommend a few starting points for building a security program.
The authoritative framework published as part of ISO 27001 and 27002 lists numerous controls, many of which are relevant to enterprises looking to manage information security risks. Yet, where should one start? Which of the measures are most important, providing the most bang for the buck? ISO 27001 highlights the importance of undergoing a risk assessment to decide which of the controls are relevant for the particular organization. Unfortunately, many companies don’t know how to conduct a risk assessment or, having conducted one, didn’t get much out of the exercise.
Are there any security controls that are so essential, that they should apply to most environments? PCI Data Security Standard (DSS) attempts to provide such guidance, but even that prescriptive document can be overwhelming to many organizations. Is there a simpler starting point?
A Quick Look at 3 Security Projects
Seeking to understand which security controls are deemed to be particularly useful by my peers, I looked at the following projects:
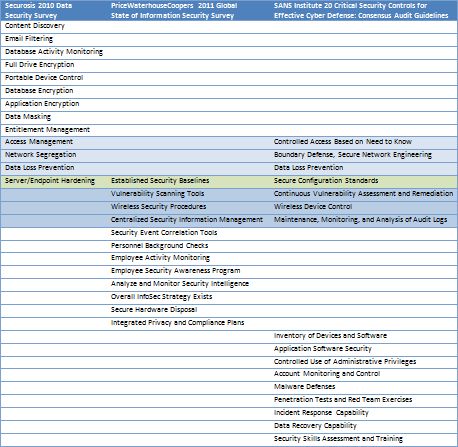
- Securosis 2010 Data Security Survey: Securosis put together a list of important data security controls to assess which of them are perceived to be most effective by survey respondents. (For Securosis’ control selection criteria, see page 34 of their report.) The survey focused on the security measures for protecting data and did not examine other, such as infrastructure security measures. Observation: Data Leakage Prevention (DLP), full disk encryption, Web Application Firewalls (WAFs) and server/endpoint hardening are among the data-centric controls that survey participants considered most effective.
- PwC 2011 Global State of Information Security Survey: PriceWaterhouseCoopers asked survey participants about several infosec capabilities to assess which of the capabilities are actually in place. (I consider “capability” to be synonymous to “control” in this context.) Observation: In 2010 organizations maintained the status quo with respect to the comprehensiveness of their security programs; PwC’s findings suggests the advancement of security capability deployment has stalled. (See page 28 of the report for details.)
- SANS Institute 20 Critical Security Controls: SANS, in cooperation with a number of US Federal agencies, defined a “prioritized baseline of information security measures and controls that can be continuously monitored through automated mechanisms.” The listing of controls and associated guidelines were designed to reflect the attack vectors most relevant to US Federal enterprise environments. Disclaimer: I’m a member of SANS faculty and was peripherally involved with the effort.
Each organization used different approaches for determining which controls to focus on, and I cannot directly compare the listing of security measures produces as part of these independent efforts. However, I feel comfortable using them to assess which security measures come to mind of security professionals when they are asked to prioritize controls.
Highlighting a Few Security Controls
There was one security control that was present in all 3 listings, though in slightly different forms: The definition and enforcement of security standards for the configuration and hardening of computer systems. Not only can this make the system more resilient to a compromise, but also this step can act as a starting point for a change management program. An unwanted change—a deviation from the baseline—can make the system more vulnerable and might, in itself, be an indicator of compromise.
Another control that I’d like to highlight is the centralized collection and monitoring of security events. (It was mentioned in 2 listings.) Without having visibility into what goes on within your environment, you will have a hard time identifying policy violations, noticing security incidents and responding to intrusions.
I’d also like to mention the need to establish a vulnerability management program to identify and remediate security configuration weaknesses and missing security patches.(This control was present in 2 listings.) Many attacks succeed by taking advantage of security vulnerabilities for which patches existed, but weren’t applied.
Lastly, it’s worth pointing out the need to monitor and restrict the distribution of sensitive data throughout the enterprise, especially as it is transported out of the network or through the use of removable media. (This control was in 2 listings under the heading of Data Leakage Prevention, a.k.a. DLP.) Even of attackers bypass your other security controls and access sensitive data, you may be able to detect and block their attempts to exfiltrate the data out of the environment.
Perhaps these few controls present a good start that applies to many enterprises. Many more controls are necessary to establish an effective information security program and, as pointed out by ISO 27001, their selection and implementation should be based on the risk assessment conducted by the organization.
Listing of Controls from the 3 Security Projects
Below is my summary of the controls referenced in the security projects I mentioned above. The reason for the limited overlap is mostly because the controls were selected using different criteria and for different purposes. Also, I think it highlights the difference in opinions across the information security industry.
To view the large version of the table, click the image.