How the Scarcity Principle is Used in Online Scams and Attacks
The scarcity principle—people value less available opportunities more—powers online scams: fake expiration countdowns, CAPTCHAs before malware downloads, and login screens blocking desired content. Obstacles and time limits trigger psychological reactance, making people work harder to obtain what they're denied.
The scarcity principle, popularized in Robert Cialdini’s book Influence: Science and Practice, dictates that people assign more value to opportunities that are less available. Scammers take advantage of this psychological tendency when social engineering victims on-line.
Time Limitation
A classic illustration of the scarcity principle used for persuasion is the situation where the offer has an expiration date. You’ve probably seen this in action at a local store, where signs exclaimed “Hurry! Sales ends Saturday!” How do scammers replicate this scenario on line?
In an earlier post I described a “Home Income Kit” scam, which attempted to persuade victims to pay for a kit that would allow them to make thousands of dollars per month without much effort. The scam used numerous social-engineering techniques. One of them was the scarcity principle in this form:

The scarcity principle suggested that people were more likely to purchase the kit before the (bogus) promotion offer was about to expire.
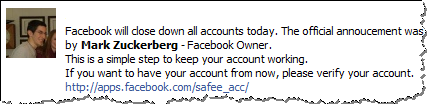
Another illustration of the time limitation igniting the sense of urgency among victims is the scam that directed people to a fraudulent website under the guise that Facebook will be disabling unconfirmed accounts today. (This scam was reported by Graham Cluley.)
Obstacle Restriction
Building upon the scarcity principle, Cialdini described research showing that “the act of limiting access to a message causes individuals to want to receive it more.” In other words, the forbidden fruit tastes sweeter.
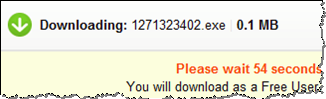
I noticed this principle being used as part of an on-line scam that Jerome Segura described, discussing a link to a malicious executable that was sent via email. When the victims clicked the link, they were made to wait a minute:
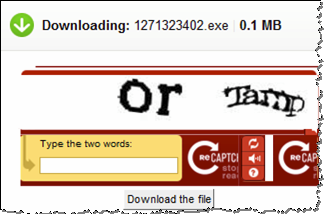
After that, they had to solve a CAPTCHA challenge before finally being allowed to obtain the file. The more obstacles the victim had to bypass, the more he or she wanted the file:
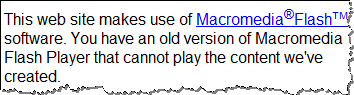
Similar use of the scarcity principle occurs when victims are told that they need to install a missing plug-in or update Flash Player to see the desired content. Not being able to get the content immediately makes people want it even more. Unfortunately, they end up installing a trojan horse in the process.
We can consider the scarcity principle playing a role in the success of phishing scams, which present the victim with a logon screen before the person can access the needed data. The human brain will see the logon screen as an obstacle that’s restricting access to the desired item, and will motivate the person to provide the username and password to bypass the restriction.
Why the Scarcity Principle Works
According to Cialdini, one of the reasons the scarcity principle works is because “things that are difficult to attain are typically more valuable.” As the result, humans use the availability of an item as a heuristic for assessing its quality.
Second, “as things become less accessible, we lose freedoms. According to psychological reactance theory, we respond to the loss of freedoms by wanting to have them.”
Now that you know about the scarcity principle, be weary of the situations where someone is trying to use it to persuade you to take an action. Also, consider discussing this tendency and the examples of relevant scams as part of your security awareness training.
If you found this post interesting, take a look at my other writing on social engineering, including Faux-Targeted Attacks and the Magic of Cold Reading.