Considering that attackers have been successful at exploiting client-side vulnerabilities, enterprises should take the time to locate and patch outdated installations of targeted programs such as Adobe Reader and Java. Most vulnerability scanning tools let administrators do this. Sometimes, especially when dealing with a malware outbreak, it helps to have lightweight, standalone tools for the task.
HBGary’s AcroScub is a free utility like this—a single command-line executable that can scan Windows hosts and find Adobe Reader instances that should be patched. The tool uses WMI for remotely accessing systems without requiring an agent on the assessed system. Though this method is a pain to use on computers that aren’t part of a Windows Domain, most enterprise environments will shouldn’t have WMI access issues.
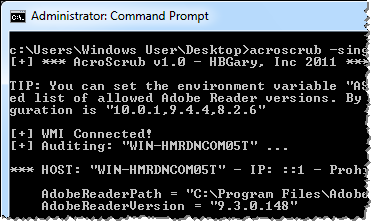
AcroScrub allows the user to specify logon credentials and to use the ASAllowedVersions environment variable for overriding the version values that it considers outdated. The tool saves its output to the auditresults.txt file:
*** HOST: “WIN-HMRDNCOM05T” - IP: ::1 - Prohibited Adobe Reader Version ***
AdobeReaderPath = “C:Program FilesAdobeReader 9.0ReaderAcroRd32.exe”
AdobeReaderVersion = “9.3.0.148”
For more usage details, see the README file that is part of the AcroScrub distribution archive.
An administrator or incident responder could use the tool to remotely scan the enterprise environment for Adobe Reader versions. Alternatively, the tool could be launched to scan users’ systems through the use of logon scripts or scheduled tasks.
When I first saw the tool, I thought it might be easy to recreate its functionality using PowerShell by examining registry values. It seems, however, that this is easier said than done. You would first need to find and read the Reader’s ENU_GUID registry key. You would then have to translate that GUID into a corresponding version number, as documented by Adobe. (Do you know a better way to do this? How about locating old Java versions?)
Two annoyances that I encountered in regards to AcroScrub:
- To download the tool you need to have an account on HBGary’s Support Center site. Registration is free, but requires validation of your mobile phone number.
- It would be convenient if the tool could provide its output in a computer-readable format, such as XML or CSV.
I recommend using a full-fledged vulnerability scanner to locate vulnerable software. However, if you’re in the middle of a security incident that involves Adobe Reader, AcroScrub might be a useful addition to your toolkit. Just be sure to try it in advance to confirm that it works in your environment and that you know how to use it.