PDF files designed for infecting computer systems can include a malicious Flash/SWF program that's designed to aid in exploiting a vulnerability in Adobe Reader or Flash Player. In an earlier article I explained how to extract SWF object from a PDF file using PDF Stream Dumper and pdf-parser. A new tool SWF Mastah, by Brandon Dixon, can assist with this process as well.
SWF Mastah makes use of Brandon’s PDF X-RAY framework and Jose Miguel Esparza's Peepdf tool and to handle complex PDF files even in situations where pdf-parser might fail at locating or extracting the SWF object. Here's a quick example, which uses the malicious PDF file “The Obama Administration and the Middle East.pdf” that was documented on Contagio Malware Dump.
SWF Mastah (a.k.a. swf_mastah.py) can scan the PDF file, automatically locate a Flash object and extract it, all in one step:
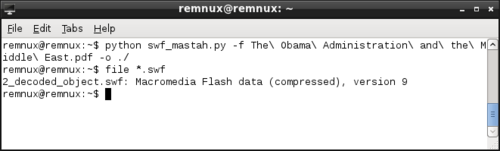
The screen shots above show SWF Mastah running on the REMnux. For another example of SWF Mastah in action, see Brandon's blog posting in which he introduced the tool to the world.