When orchestrating phishing attacks, scammers sometimes register domain names similar to those of the targeted organizations, in the hopes of exploiting victims' typos or inattention. Therefore, it's a good idea to keep an eye on your company's domain name variations and perhaps preemptively register some of them. Let's take a look at how domain name variations could be generated by you as well as the attackers.
Experimenting With Domain Name Variations
The command-line tool dnstwist by Marcin Ulikowski provides a convenient way for generating domain name variations using a range of techniques. To use dnstwist, you need to have Python on your system, along with a couple of libraries. If running Ubuntu, you can install dnstwist and its dependencies like this:
sudo apt-get install python-dnspython python-geoip python-whois python-requests git clone https://github.com/elceef/dnstwist.git cd dnstwist
In addition to generating domain name variations, dnstwist can examine whether copycat domains are hosting content similar to the real site. To use this capability, you'll need to install the Python ssdeep library, as explained on the tool's website.
Once dnstwist is installed, you can run the command "./dnstwist.py" while in the tool's directory, specifying the domain name whose variations you'd like to generate as the parameter. You can also specify the optional parameter "csv" if you'd like to see the output in a comma-separated values format. For instance here's how I used dnstwist to see variations of my domain "zeltser.com":
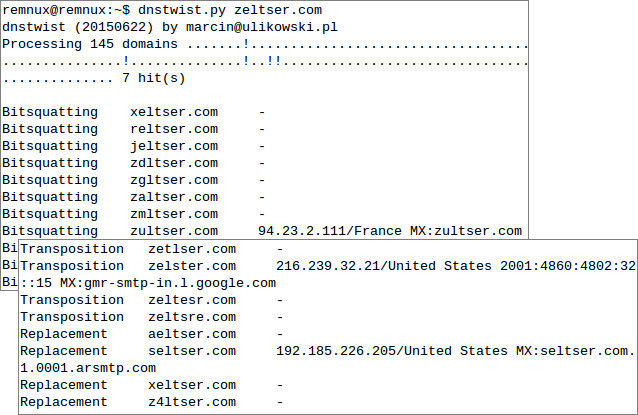
When dnstwist notices that one of the generated names is registered, it shows details about it, such as the IP address that corresponds to it and its likely geographic location. (I'd love to also be able to see when the record was most recently created or updated.)
If you invoke dnstwist with the "-w" parameter, the tool will perform Whois queries for each active domain and display when its record was created and updated. Note that in the screenshot above, I ran the tool as "dnstwist.py", instead of "./dnstwist.py", because I added the tool's directory to my PATH variable.
Domain Name Variation Techniques
We can look at the algorithms implemented by dnstwist to understand what approaches adversaries could use for generating domain name variations. These include the following approaches:
- Bitsquatting, which anticipates a small portion of systems encountering hardware errors, resulting in the mutation of the resolved domain name by 1 bit. (e.g., xeltser.com).
- Homoglyph, which replaces a letter in the domain name with letters that look similar (e.g., ze1tser.com).
- Repetition, which repeats one of the letters in the domain name (e.g., zeltsser.com).
- Transposition, which swaps two letters within the domain name (e.g., zelster.com).
- Replacement, which replaces one of the letters in the domain name, perhaps with a letter in proximity of the original letter on the keyboard (e.g, zektser.com).
- Ommission, which removes one of the letters from the domain name (e.g., zelser.com).
- Insertion, which inserts a letter into the domain name (e.g., zerltser.com).
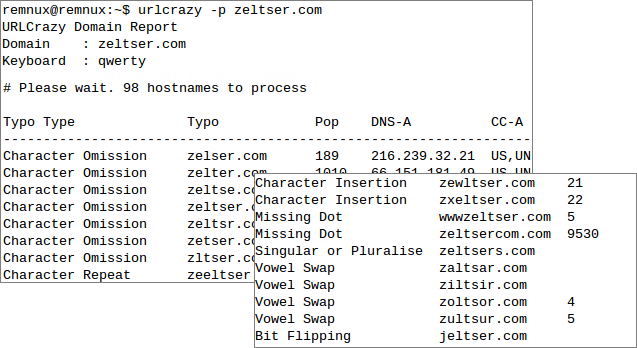
A good supplement to dnstwist is the command-line tool URLCrazy by Andrew Horton, which implements the following techniques in addition to some of the methods outlined above:
- Missing dot, which removes a dot from the domain name (e.g., zeltsercom.com).
- Singularization or Pluralization, which adds or removes "s" at the end of the domain name (e.g., zeltsers.com).
- Vowel swap, which replaces a vowel within the domain name (e.g., zultsur.com).
- Wrong TLD, which replaces the top-level domain suffix (e.g., zeltser.ca).
One of the nice features of URLCrazy is its attempt to rank the popularity of the generated active domains according to Google search results. Installing this tool, as outlined on its website, requires having Ruby on your system, which is easy to obtain.
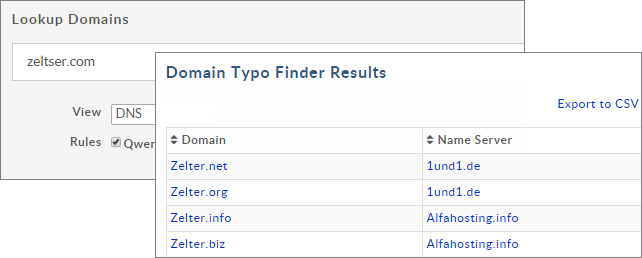
If you don't want to install software locally to generate names, take a look at the web-based tool Domain Typo Finder, available for free from DomainTools. It implements methods based on letter replacement, transposition, repetition and homoglyphs.
Explore Name Variations for Pen Tests and Defense
Adversaries (and penetration testers) can employ numerous approaches to generating domain names that, at a quick glance, will appear similar to the targeted organization's domain. Potential victims in the organization might also reach attackers' systems residing at these domains by making a typo. If you're defending your organization from phishing and related attacks, keep an eye on your domain name's variations. Either register some of them yourself or make sure you're notified when a risky name pops into existence, possibly as a precursor to an attack.