Which Apps Are Authorized to Access Your Social Networking Accounts?
Attackers may target less secure third-party apps authorized to access social networking accounts rather than attacking the platforms directly. Periodically review and deauthorize unused apps on LinkedIn, Facebook, and Twitter—when in doubt, remove access since reauthorization is easy.
Instead of pursuing vulnerabilities present directly in Facebook, Twitter or LinkedIn, attackers might find it easier to identify problems in less mature websites and apps designed to integrate with the targets’ social networking accounts. From the user’s perspective, it’s easy to forget about the myriad of sites that the person may have authorized to have read or write access to his social networking profile.
Follow the steps below to review which apps you’ve authorized to access your Facebook, Twitter and LinkedIn accounts. Check this list periodically and deauthorize the services you no longer use. When in doubt, remove access—when you use the site or app that relied on that access, you should be able to easily reauthorize it.
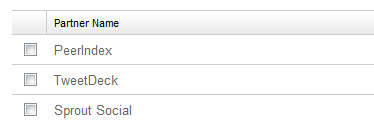
Access the Authorized Applications page by hovering over your name in the upper right corner of the LinkedIn site. Select Settings. In the bottom left corner select Groups, Companies & Applications. Select “View your applications”.
Access the Application Settings page by clicking on the Account button in the upper right corner on the Facebook site. Select Account Settings. On the left side of the screen select Applications.

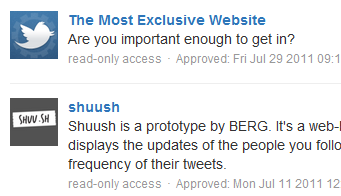
Access the Connections page by clicking on your name in the upper right corner of the Twitter site. Select Settings, then select the Applications tab.