The Dark Side of Remote Desktop
The Morto worm spread by scanning for RDP on port 3389 and brute-forcing Administrator passwords using common credentials. Tools like TSGrinder and Ncrack automate RDP password attacks. Mitigations include requiring VPN access, using non-default ports, strong passwords, and account lockout policies.
Organizations large and small often make use of Remote Desktop or Terminal Services to remotely connect to Windows computers over the Internet and internally. These tools use Microsoft’s RDP protocol to allow the user to operate the remote system almost as if sitting in front of it. Such capabilities are helpful for not only legitimate users, but also for attackers.
The Internet community saw a reminder of the dark side of RDP due to the emergence of the “Morto” worm. According to F-Secure, a system infected with the worm scans the local network for systems listening on TCP port 3389 and, when it does, attempts to login to them via RDP by guessing the Administrator password. The worm uses a list of common 30 passwords, which include favorites such as “password” and “12345678”.
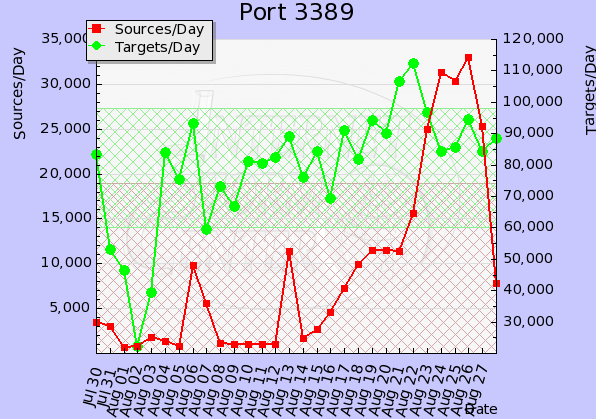
The emergence of this worm correlates with the increased volumes of TCP port 3389 traffic, reported by SANS Internet Storm Center a few days prior to the F-Secure report:
The propagation approach employed by “Morto” is often used by penetration testers and human attackers alike: access the remote host by brute-forcing the password. One free tool that can automate this process is TSGrinder. You can see TSGrinder in action in the video below. Note that TSGrinder is relatively slow, and requires that an older version of Remote Desktop client be installed on the attacking system.
A more modern (and faster) tool for remotely brute-forcing RDP credentials is Ncrack. Ncrack is a command-line tool that also supports a variety of other protocols, including SSH, VNC and FTP. In addition to being available in the source code form, Ncrack can be downloaded in a compiled form for Windows and OS X. (Update: For more on using Ncrack for RDP cracking, see Chris Gates’s post on the Carnal0wnage blog.)
Brute-forcing passwords on the internal network using tools such as TSGrinder and Ncrack is often quite effective. The approach also works over the Internet in many cases, because organizations often expose TCP port 3389 for remote access to workstations and servers over the Internet.
We can use the emergence of the “Morto” worm as a reminder to examine the use of Remote Desktop for remote access to systems over the Internet. Consider requiring an authenticated VPN connection before anyone has the ability to connect to this service. If you have to expose the service to the Internet without a VPN, don’t use the default port TCP 3389—instead pick a random high-numbered port. And, it goes without saying, use strong passwords and non-Administrator accounts.
Lastly, consider configuring user accounts for auto-lockout after a number of unsuccessful logon attempts, while recognizing the potential for a denial of service attacks when the attacker could trigger such a condition remotely.
Hand-picked related items: