
My new writing course for cybersecurity professionals teaches how to write better reports, emails, and other content we regularly create. It captures my experience of writing in the field for over two decades and incorporates insights from other community members. It's a course I wish I could've attended when I needed to improve my own security writing skills.
I titled the course Cybersecurity Writing: Hack the Reader. Why "hack"? Because strong writers know how to find an opening to their readers' hearts and minds. This course explains how you can break down your readers' defenses, and capture their attention to deliver your message—even if they're too busy or indifferent to others' writing.
Here are several examples of such "hacking" techniques from course sections that focus on the structure and look of successful security writing:
- Headings: Use them to sneak in the gist of your message, so your can persuade your readers even if they don't read the rest of your text.
- Lists: Rely on them to capture your readers' attention when they skim your message for key ideas.
- Figure Captions: Include them to influence the conclusion your readers reach even if they only glance at the graphic.
This is an unusual opportunity to improve your writing skills without sitting through tedious lectures or writing irrelevant essays. Instead, you'll make your writing remarkable by learning how to avoid common pitfalls.
For instance, this slide opens the discussion about expressing ideas clearly, concisely, and correctly:
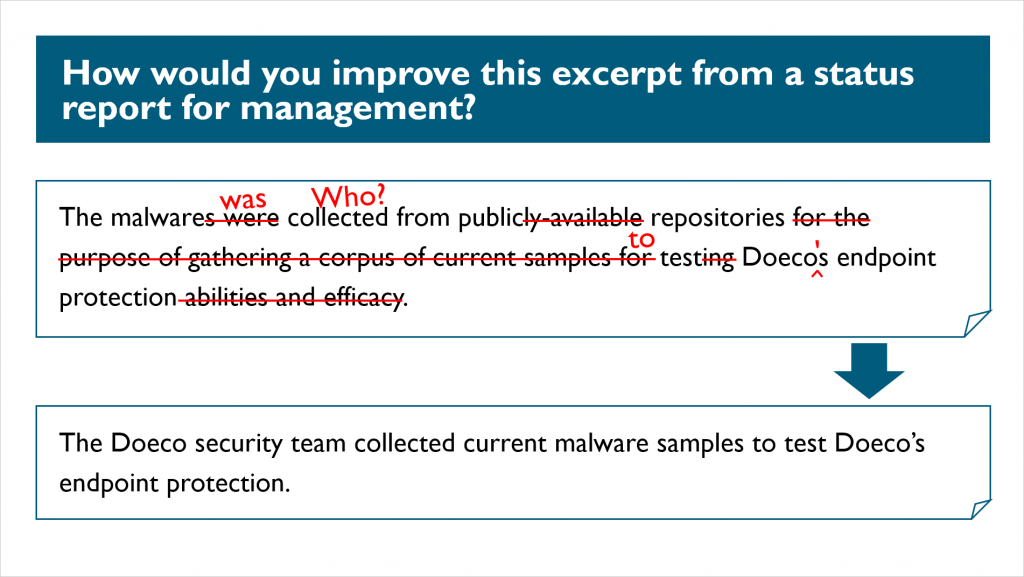
This course is grounded in the idea that you can become a better writer by learning how to spot common problems in others' writing. This is why the many examples are filled with delightful errors that are as much fun to find as they are to correct.
One of the practical takeaways from the course is a set of checklists you can use to eliminate issues related to your structure, look, words, tone, and information. For example:

The course will help you stand out from other cybersecurity professionals with similar technical skills. It will help you get your executives, clients, and colleagues to notice your contribution, accept your advice, and appreciate your input. You'll benefit whether you are:
- A manager or an individual team member
- A consultant or an internally-focused employee
- A defender or an attacker
- An earthling or an alien
You can now attend this course (SEC402) online at SANS Institute.