Controlling Adobe Acrobat/Reader JavaScript Support
Disabling JavaScript in Adobe Acrobat/Reader renders many PDF exploits ineffective. If full disabling isn't practical, Adobe's JavaScript Blacklist Framework lets users selectively disable risky API calls via registry entries, which enterprises can distribute through Group Policy.
PDF documents’ support for executing embedded JavaScript has been abused by malware authors to exploit numerous vulnerabilities in Adobe Acrobat and Reader products. Disabling JavaScript support renders many of these exploits ineffective. If disabling JavaScript outright isn’t practical for business reasons, end-users and enterprise administrators can blacklist risky JavaScript APIs with relative ease.
End-Users Adobe Acrobat/Reader JavaScript Controls
Individual users can easily disable Adobe Acrobat/Reader’s support for JavaScript through the Preferences menu. Note that although this step will disable many PDF exploits, some exploits could function even with JavaScript disabled, so restricting JavaScript isn’t the the only step you need to take to safeguard the system.
If the person doesn’t wish to completely disable JavaScript out of fear that some important documents won’t render properly, he can selectively disable the most dangerous JavaScript API calls. Adobe’s JavaScript Blacklist Framework for Adobe Acrobat or Reader utility for Microsoft Windows makes this easy. It presents the user with a listing of risky API tools, allowing the person to select those that should be disabled.
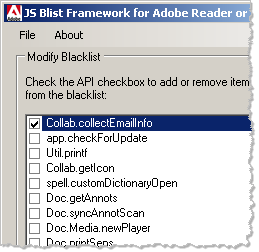
Behind the scenes, this utility adds local registry entries that disable the corresponding API calls. You can do this manually if you know what you’re doing; the utility makes this easier to do for most people.
Enterprise Control of Adobe Acrobat/Reader JavaScript
Adobe’s Application Security for the Acrobat Family of Products manual documents how to create registry entries for preventing JavaScript from being able to make specific API calls. Depending on the environment and intent, the registry key that needs to be modified on a 32-bit Windows system can be:
HKLMSOFTWAREPoliciesAdobe<product><version>FeatureLockDowncJavaScriptPermstBlackList
HKLMSOFTWAREAdobe<product><version>JavaScriptPermstBlackList
On 64-bit systems the key is located under HKLMSOFTWAREWow6432NodeAdobe.
These are the keys that get modified on the user’s behalf by the JavaScript Blacklist Framework for Adobe Acrobat or Reader tool. For instance, disabling Collab.collectEmailInfo creates results in the following registry key when Adobe Reader 9 is installed: “HKLMSOFTWAREPoliciesAdobeAcrobat Reader9.0FeatureLockDowncJavaScriptPermstBlacklist” contains “Collab.collectEmailInfo”
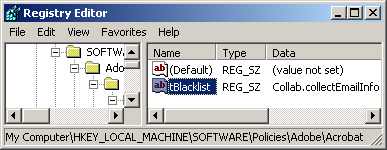
Because Adobe Acrobat/Reader JavaScript API blacklisting on Windows is done through the registry, enterprise administrators can use Group Policy in an Active Directory environment to distribute these settings company-wide. (For more on this, see Adobe’s Acrobat Enterprise Administration Guide.)
The administrator can also proactively blacklist risky API calls, such as those listed in the JavaScript Blacklist Framework for Adobe Acrobat or Reader tool. Also, when dealing with a security incident, the organization can examine the malicious PDF to understand the exploit and then blacklist the corresponding JavaScript API call, if appropriate.
Hand-picked related items:
- Enterprises Won’t Adopt Adobe Reader X Any Time Soon
- AppLocker for Containing Windows Malware in the Enterprise
- Deploying Google Chrome in the Enterprise
If the topic of locking down risky software in the enterprise interests you, take a look at the 2-day Combating Malware in the Enterprise course I co-authored with Windows security expert Jason Fossen.