Clickjacking—the practice of deceptively directing a website visitor’s clicks to an undesired element of another site—is surprisingly effective. It's been often used to propagate links to malicious websites on Facebook. More recently, similar techniques have been shown effective in de-anonymizing website visitors and even tricking them into granting attackers access to OAuth-secured data. Let’s see what such attacks entail.
Classic Clickjacking to Propagate Links on Facebook
In a classic clickjacking scenario, an attacker establishes a malicious website that invisibly embeds the Facebook "Like" or "Share" button in a transparent iframe. The iframe floats over a page element that the victim is likely to click on; alternatively, the invisible iframe follows the mouse cursor. When the victim clicks within the malicious site, the click is directed to the invisible "Like" or "Share" button. This approach isn’t limited to Facebook interactions, of course, as the attacker can embed elements from other sites in the iframe.
Consider a message below, which is typical of what you might see on Facebook if one of your connections was trapped by a clickjacking site:
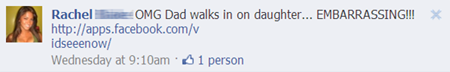
Wondering why your friend might share a link with you, you click on it, only to find yourself on a site that seems to embed a YouTube video. However, you probably won't see the Facebook "Like" buttons that I revealed when taking the screenshot below:
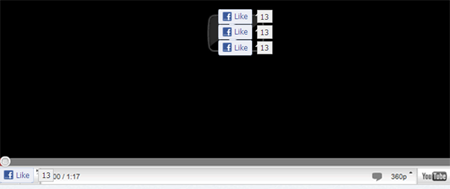
The "Like" buttons are floating over the two locations where the person is likely to click to play the video: in the middle of the supposed video player and in the bottom left corner. The actual victim wouldn't see these buttons, because they would be invisible in a transparent iframe. By attempting to play this video, the person will actually press the "Like" button, increasing this site’s visibility on Facebook.
Newer Variations of Clickjacking Techniques
In a paper Clickjacking Attacks Unresolved, Lin-Shung Huang and Collin Jackson document more insidious variations of clickjacking attacks. For instance, they provide a proof-of-concept demonstration how an attacker can determine the identity of the visitor to the malicious website by asking Facebook for this information.
I captured this Facebook User De-anonymization demo in the video below. The video shows the Facebook "Like" button following the victim's mouse cursor; in a real attack, the button would be invisible.
When the person inadvertently clicks the "Like" button, he becomes a fan of the attacker's Facebook page. Then, according to the paper:
"The attacker's web page is notified when the victim clicks on the Like button via FB.Event.subscribe('edge.create', …), triggering the attacker's server to pull the fan list from his Facebook page and identify the newly added fan. The attacker's server queries the user's public profile via Facebook Graph API, and then removes the user from the fan list."
This allows the attacker to obtain to identifying information about the person, such as name, gender, local and Facebook ID. The paper's authors demonstrate that a similar attack works using the Twitter "Follow button:

Clickjacking and Timing Attacks
Huang and Jackson also describe a click-timing attack called double-clickjacking, which can be used to trick the victim into authorizing the attacker's authorization request to third-party OAuth providers. This approach works even when websites implemented some of the common iframe-focused clickjacking defenses, such as X-Frame-Options. According to the paper,
"Although the attacker can no longer embed the approval page in an IFRAME, it is possible to load the [OAuth] approval page in a pop-under window. A pop-under window is a basically a popup window that is hidden behind the main browser window right after it was opened. Since modern browsers block popup windows unless triggered by user-initiated clicks, we require multiple clicks in this specific attack to bypass popup blockers."
To see the proof-of-concept code of double-clickjacking in action, follow the link in the Clickjacking Attacks Unresolved paper.
What to Do About Clickjacking?
Clickjacking incidents affect many people, and are unlikely to subside. To date, most of these attacks have been used for distributing malicious links on Facebook. However, the same approaches can be used for more insidious scenarios, as Huang and Jackson have demonstrated. Their paper outlines some of the approaches that the developers of websites and browsers can use to mitigate clickjacking risks; however, these techniques are far from being comprehensive. Worst of all, it’s hard to come up with practical advice to end-users to avoid getting hit by this attack vector. Advising people not to click on web page elements isn't really an option.