As much as we try to be proactive about information security, IT planning, or project management, we get distracted, or procrastinate. These information security cheat sheets, checklists and templates are designed to assist IT professionals in difficult situations, even if they find themselves unprepared.
Writing Tips for IT Professionals
This cheat sheet offers practical tips for IT professionals seeking to improve their writing skills.
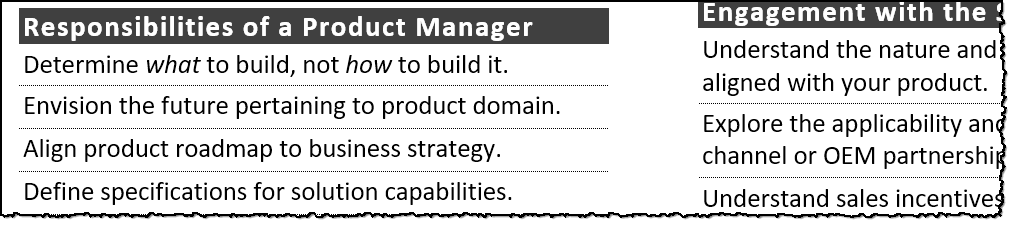
Tips for Creating and Managing New IT Products
This cheat sheet offers practical advice for product managers tasked with launching new information technology solutions at startups and enterprises.
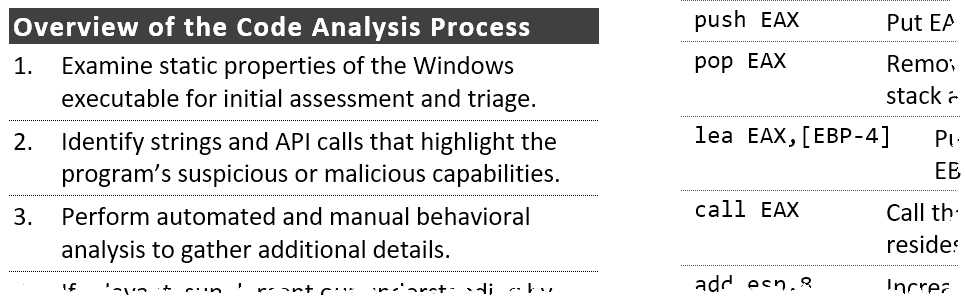
Tips for Reverse-Engineering Malicious Code
This cheat sheet outlines tips for reversing malicious Windows executables via static and dynamic code analysis with the help of a debugger and a disassembler.
Tips for Getting the Right IT Job
Practical tips for finding and getting the right job in information technology:
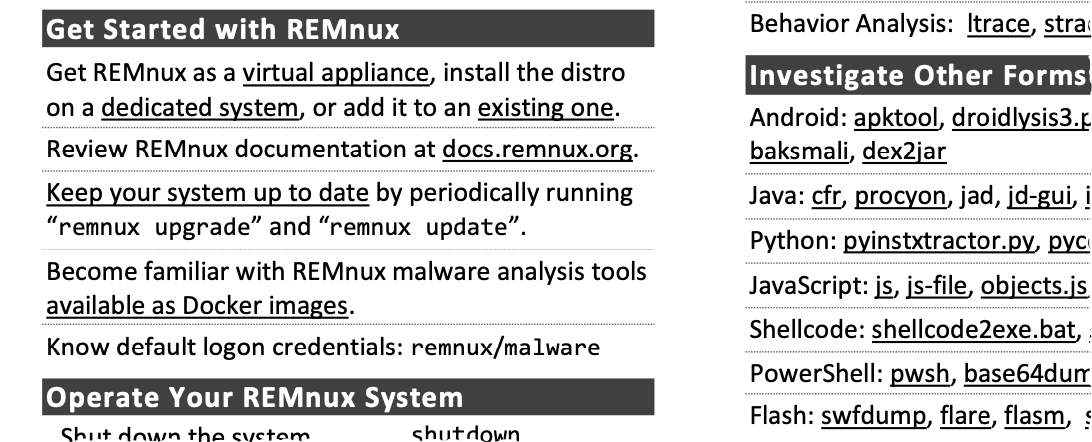
REMnux Usage Tips for Malware Analysis on Linux
Key tools and commands for analyzing malicious software on the REMnux Linux distribution:
Tips for Creating a Strong Cybersecurity Assessment Report
This cheat sheet offers advice for creating a strong report as part of your penetration test, vulnerability assessment, or an information security audit.

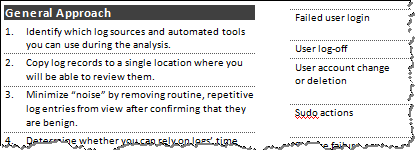
Critical Log Review Checklist for Security Incidents
Checklist for reviewing critical logs when responding to a security incident. It can also be used for routine log review, co-authored with Anton Chuvakin:
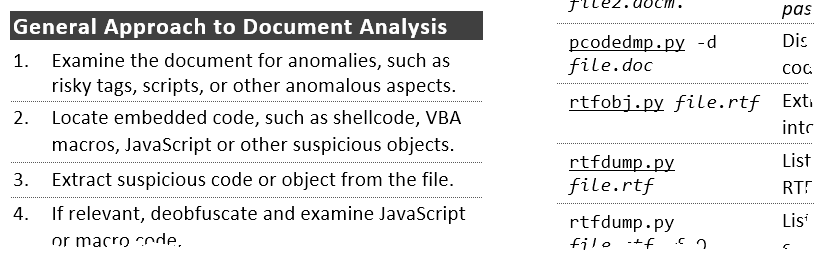
Cheat Sheet for Analyzing Malicious Documents
Tips and tools for analyzing malicious documents, such as Microsoft Office, RTF and Adobe Acrobat (PDF) files:
Security Architecture Cheat Sheet for Internet Applications
Tips for the initial design and review of a complex Internet application's security architecture:
Troubleshooting Human Communications
Communication tips for technologists, engineers, and information workers:
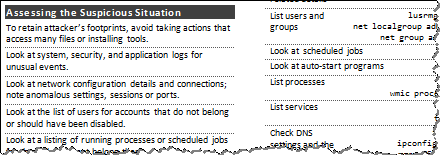
Security Incident Survey Cheat Sheet for Server Administrators
Tips for examining a potentially-compromised server to decide whether to escalate for formal incident response:
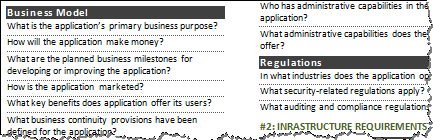
Initial Security Incident Questionnaire for Responders
The questions the incident handler should consider asking when taking control of a qualified incident:
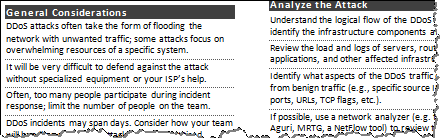
Network DDoS Incident Response Cheat Sheet
Advice for battling a network DDoS attack on your infrastructure:
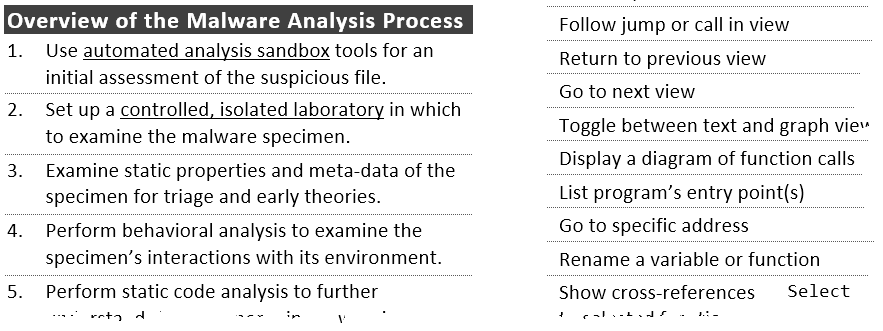
Malware Analysis and Reverse-Engineering Cheat Sheet
Shortcuts and tips for analyzing malicious software:
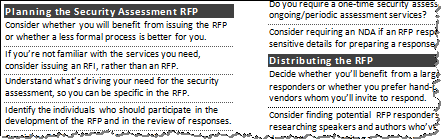
Information Security Assessment RFP Cheat Sheet
Tips for planning, issuing and reviewing RFPs for information security assessments:
How to Suck at Information Security
Common information security mistakes, so you can avoid making them:
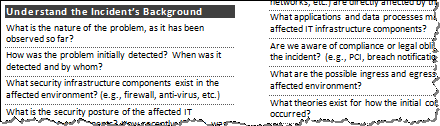
Report Template for Threat Intelligence and Incident Response
A report template and framework for for capturing key details related to a large-scale intrusion and documenting them in a comprehensive, well-structured manner.