Learn Better Security Breach PR from Harold Sun's Halfhearted Apology
Herald Sun's website was compromised to serve rogue antivirus, but their brief apology offered few details and underplayed the risk. Better post-incident communications require promptness, clarity, and openness—clarify which malware was involved, offer specific cleanup recommendations, and explain measures to prevent recurrence.
The website of Australia’s Herald Sun newspaper was compromised and used to attack its visitors on July 11, 2011. The newspaper reacted within a day or so, though its communications to its readers regarding the incident leave room for improvement. Let’s see what we can learn regarding security breach PR from this event.
Herald Sun’s Brief Apology
A few days after the incident, the newspaper posted a brief apology for the incident at the bottom right corner of its website for about a day, though it has now disappeared from the site:
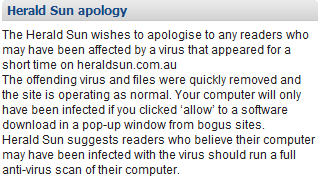
Though Herald Sun’s apology offers few details regarding the incident, one can surmise that it involved a rogue antivirus scam, attempting to trick website visitors to install malicious software.
Follow-Up Statement from Herald Sun
The newspaper offered a few tidbits regarding the breach in a follow-up statement, confirming that the “attack attached malware on some files on the site.” This suggests that the problem wasn’t due to a malicious ad served by a third party; if it were, the company would be quick to displace the blame on the appropriate advertising network. Herald Sun further stated that:
“We have since addressed the issue, but we are not in a position to release any further details on the basis that it may provide information for further attacks.”
It’s not uncommon for organization to refuse providing data breach information in the name of security. If I were to nitpick on the Herald Sun’s statement, I’d say that if the issue had been addressed, then there would be little risk to shedding some light on the nature of the attack.
Ways of Improving Post-Incident Communications
Herald Sun’s post-incident communications reflect the typical PR approach of positioning the breach as a non-significant event. After all, in the words of the newspaper, its readers would only be affected if they clicked “Allow” to let malware install itself on their computers. In reality, social engineering scams are highly effective, especially with non-technical computer users, into persuading them to install rogue antivirus tools.
The newspaper’s suggestion of merely running an antivirus tool is akin to recommending that victims of data theft sign up for identity-monitoring service—the damage has already been done.
At the very least, Herald Sun should have clarified which malware was targeting its readers and offered specific recommendations for the tools that might be able to clean it up. Also, I would want the organization to make a stronger statement regarding the measures it is implementing to mitigate the risk of similar incidents occurring in the future.
In the words of Paul Ducklin, promptness, clarity, and openness should be the key elements of a company’s response to an information security breach. It’s great to see Herald Sun exercise promptness, but left much room for improvement regarding other aspects its communications to potentially-affected readers.
Related: