SWFREtools for Analyzing Flash Malware
SWFREtools provides free utilities for reverse-engineering malicious Flash programs, including Flash Dissector for examining SWF structure and disassembling ActionScript. FP Debugger traces Flash Player execution, which can help analyze obfuscated ActionScript that deobfuscates at runtime.
SWFRETools is a promising free toolkit by Sebastian Porst for reverse-engineering malicious Flash programs. These tools are early in their development cycle and are missing features; yet, I am excited about the promise of having the more mature versions of these utilities available to malware analysts.
You can download SWFREtools in the source code form or as a compiled distribution. For an overview of SWFREtools, see Sebastian’s SOURCE Boston presentation, in which he introduced the toolkit to the world.
Flash Dissector
SWFRETools includes Flash Dissector—an interactive tool for examining the structure and contents of a SWF file.
After loading the SWF file, Flash Dissector shows the embedded tags using a tree listing on the left side of the screen. It also shows the hex view of the file’s content on the right side.
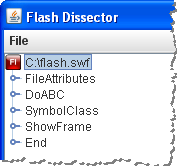
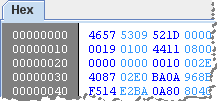
If you select a tag that includes ActionScript—namely, DoABC or DoAction—Flash Dissector will show you the disassembled version of ActionScript. This is the area where the tool leaves much room for improvement: In my (limited) testing, it only presented disassembled instructions, without showing me the data being operated on.
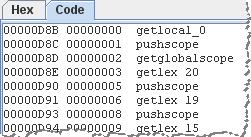
The most mature tool for examining the structure and contents of SWF files is presently SWFDump, which is a component of the free SWFToolsdistribution. I’m looking forward to seeing how Flash Dissector evolves: unlike SWFDump, it is designed specifically for dealing with malicious Flash programs.
FP Debugger
SWFRETools also includes FP Debugger—a tool designed for tracing and monitoring Flash Player during its execution. DP Debugger may help with the analysis of obfuscated ActionScript, which deobfuscates itself during runtime. This sounds very promising!
I haven’t had the opportunity to experiment with FP Debugger. If you have a chance to look explore its functionality, please share your observations.
Update: I wrote a related article explaining how to extract Flash objects from PDF files.